What is Certificate Pinning?
Certificate Pinning is the process by which native applications validate that a certificate provided by the server matches a known set of rules and conditions to ensure the integrity of data in transit and prevent unwanted sniffing of traffic by a bad actor attempting to perform a man-in-the-middle attack.
Those applications will treat all other certificates as invalid, and the TLS connection will be refused.
How does it affect my users?
If your organization uses Internet Access, the Harmony SASE agent will utilize TLS inspection to prevent questionable sites from obfuscating malicious payloads within encrypted traffic. During this process, our system issues certificates signed by Harmony SASE. As a result, applications that utilize Certificate Pinning may deem those certificates invalid and fail to create a TLS connection.
What to do?
Internet Access should be configured to bypass applications known to utilize certificate pinning. Applications can be bypassed using the following methods:
- Using the process name of the application
- A specific domain the application may be accessing
- A combination of the above methods.
To get the exact process name, do the following:
- Windows:
Open the Task Manager and search for the application. The Program name is under the Details tab.
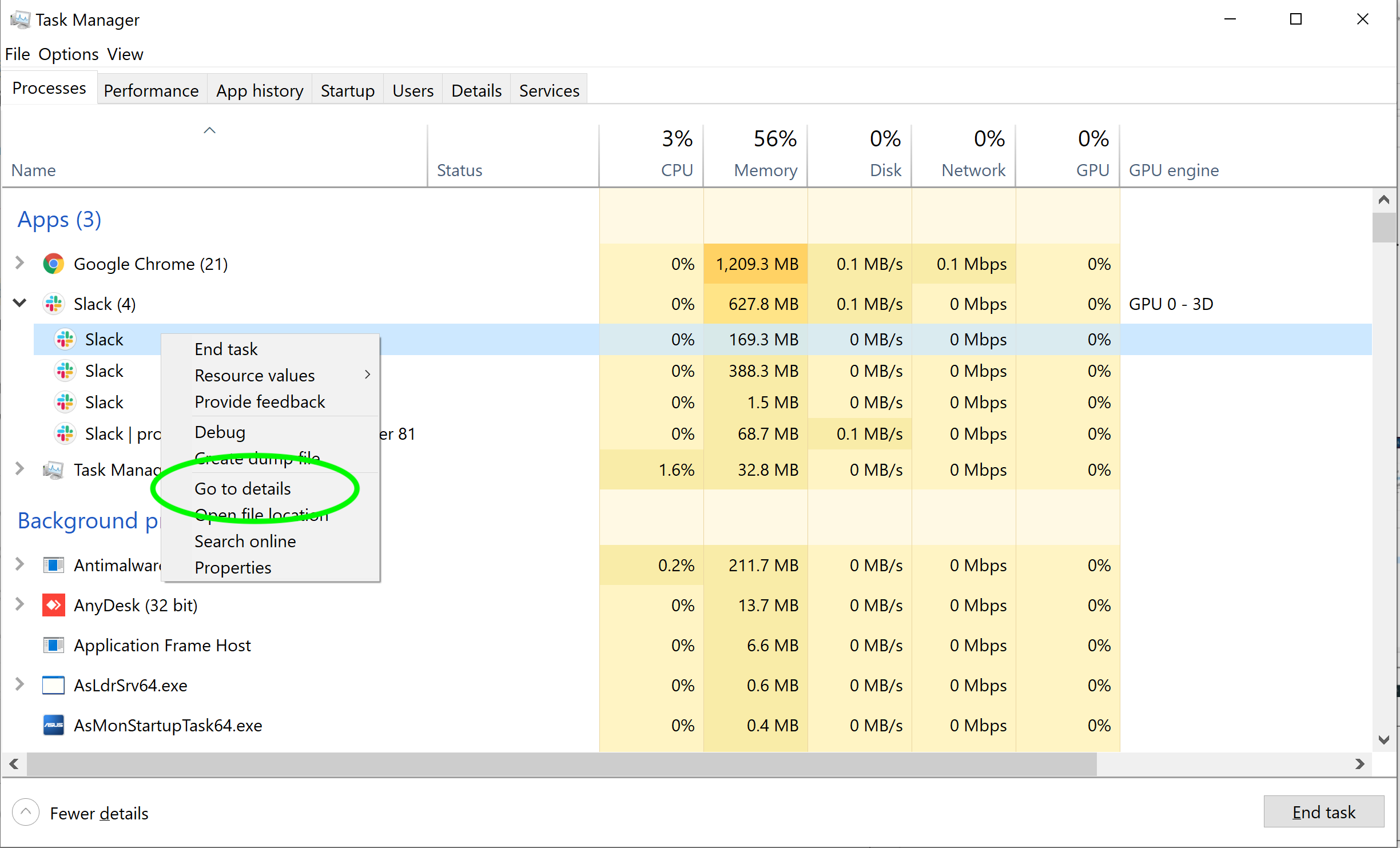
Copy the exact process name.
MacOS:
- Go to Activity Monitor > Inspect selected process > Sample > Binary Images section > first item in the list.
- Open Finder > Applications > Show Package Contents > Contents/Info.plist > Grab the string after the CFBundleIdentifier key.
Linux:
Use this command:ps aux | grep app_name
Note that the application process name to be used for bypass rule should be only the binary name itself.
Here are some examples of applications which use Certificate Pinning and bypass criteria for them:
| Application | Program | Domain |
|---|---|---|
| Adobe Suite (including Acrobat Reader, Creative Cloud and software updates) | N/A | Fill in these domain lists: List 1, List 2 |
| Apple's iMessages, iTunes, App Store, Mail | N/A | p24-keyvalueservice.icloud.com apps.apple.com itunes.apple.com mzstatic.com gs-loc.apple.com gsa.apple.com securemetrics.apple.com swscan.apple.com xp.apple.com ppq.apple.com akadns.net mail.me.com music.apple.com |
AWS Console | N/A | console.aws.amazon.com |
| Bitdefender | N/A | cdn.bitdefender.net |
| DropBox | Dropbox.exe DropboxUpdate.exe DbxSvc.exe com.getdropbox.dropbox com.getdropbox.dropbox.garcon com.getdropbox.dropbox.activityprovider com.getdropbox.dropbox.fileprovider | N/A |
| Evernote | evernote.exe | announce.evernote.com cd1.evernote.com evernote-a.akamaihd.net www.evernote.com |
| Google Drive | Windows: googledrivefs.exe macOS: com.google.drivefs com.google.drivefs.finderhelper.findersync | N/A |
Google Services | N/A | alt2-mtalk.google.com android.clients.google.com www.google.com android.googleapis.com cryptauthenrollment.googleapis.com device-provisioning.googleapis.com digitalassetlinks.googleapis.com fcmconnection.googleapis.com fcmtoken.googleapis.com firebaseperusertopics-pa.googleapis.com play.googleapis.com semanticlocation-pa.googleapis.com lh3.googleusercontent.com play-lh.googleusercontent.com gstatic.com gvt1.com |
Java Updates | N/A | sjremetrics.java.comm |
| LogMeIn | logmein.exe | Fill in this domain list |
| Microsoft Defender | N/A | Fill in this domain list |
Microsoft Lync and Skype | N/A | lync.com |
| Microsoft Office365 | Configure within Office365 under Policy > URL & Cloud App Control > Advanced Settings | For Outlook, add the following domains: office365.com, office.net, office.com |
Microsoft OneDrive | N/A | cdn.funcaptcha.com |
| Microsoft Windows Store | N/A | eus-streaming-video-msn-com wns.windows.com live.com clientconfig.passport.net wustat.windows.com windowsupdate.com msftncsi.com microsoft.com |
| Microsoft Updates | N/A | settings-win.data.microsoft.com vortex-win.data.microsoft.com delivery.mp.microsoft.com tsfe.trafficshaping.dsp.mp.microsoft.com update.microsoft.com sls.update.microsoft.com |
| Slack | Windows: slack.exe macOS: com.tinyspeck.slackmacgap com.tinyspeck.slackmacgap.helper | N/A |
| Spotify | N/A | spotify.com |
| Webex | atmrg.exe wmlhost.exe webexmta.exe washost.exe | webex.com |
| Zoom | Windows: zoom.exe macOS: us.zoom.xos | zoom.us |
Default Bypass Rules
The Default Bypass rules prevent any potential issues caused by applications and web services that are known to experience certificate pinning.
To view the complete list of default Bypass Rules, go to Web Security > Bypass Rules.
| Rule Name | Status | Source | Programs | Domains | Categories |
|---|---|---|---|---|---|
| Bypass Microsoft Teams - Pre-configured | Enabled | Any | com.microsoft.teams Teams.exe | N/A | N/A |
| Bypass sensitive traffic - Pre-configured | Disabled | Any | Any | N/A | Financial Services, Government, Health and Medicine, Legal |
| Bypass Microsoft Outlook - Pre-configured | Enabled | Programs | com.microsoft.Outlook.exe outlook.exe | N/A | N/A |
| Bypass Microsoft updates - Pre-configured | Enabled | Any | Any | settings-win.data.microsoft.com | N/A |
| Bypass Adobe updates - Pre-configured | Enabled | Any | Any | adobe.com | N/A |
| Bypass Java updates - Pre-configured | Enabled | Any | Any | sjremetrics.java.com | N/A |
| Bypass Mozilla Firefox updates - Pre-configured | Enabled | Any | Any | download-installer.cdn.mozilla.net | N/A |
| Bypass AWS console - Pre-configured | Enabled | Any | Any | console.aws.amazon.com | N/A |
| Bypass Dropbox - Pre-configured | Enabled | Programs | Dropbox.exe DropboxUpdate.exe DbxSvc.exe com.getdropbox.dropbox com.getdropbox.dropbox.garcon com.getdropbox.dropbox.activityprovider com.getdropbox.dropbox.fileprovider | N/A | N/A |
| Bypass Google services - Pre-configured | Enabled | Any | Any | alt2-mtalk.google.com | N/A |
| Bypass Google Drive – Pre-configured | Enabled | Programs | googledrivefs.exe com.google.drivefs com.google.drivefs.finderhelper.findersync | N/A | N/A |
| Bypass OneDrive - Pre-configured | Enabled | Any | Any | cdn.funcaptcha.com | N/A |
| Bypass LogMeIn - Pre-configured | Enabled | Any | Any | cdngetgo.com | N/A |
| Bypass Microsoft Lync and Skype - Pre-configured | Enabled | Any | Any | lync.com | N/A |
| Bypass Apple services - Pre-configured | Enabled | Any | Any | p24-keyvalueservice.icloud.com apps.apple.com itunes.apple.com mzstatic.com gs-loc.apple.com gsa.apple.com securemetrics.apple.com swscan.apple.com xp.apple.com ppq.apple.com akadns.net mail.me.com music.apple.com | N/A |
| Bypass Bitdefender services - Pre-configured | Enabled | Any | Any | cdn.bitdefender.net | N/A |
| Bypass Zoom - Pre-configured | Enabled | Any | Any | zoom.us | N/A |
| Bypass Webex - Pre-configured | Enabled | Any | Any | webex.com | N/A |
| Bypass Spotify - Pre-configured | Enabled | Any | Any | spotify.com | N/A |
| Check Point Updates - HTTPS bypass | Enabled | Any | Any | avupdates.checkpoint.com secureupdates.checkpoint.com updates.checkpoint.com | N/A |
| Dashlane - HTTPS bypass | Enabled | Any | Any | dashlane.com *.dashlane.com | N/A |
| Facebook – Pre-configured | Disabled | Any | Any | facebook.com | N/A |
| Finch VPN - HTTPS bypass | Enabled | Any | Any | amber.finchapi.com www.finchvpn.com | N/A |
| MyQuickCloud - HTTPS bypass | Enabled | Any | Any | *.myquickcloud.com | N/A |
| Elster de - HTTPS bypass | Enabled | Any | Any | *.elster.de | N/A |