Understanding Internet Access Policy
Internet Access policies allows you to enhance your organization's web security, using predefined categories constantly updated by Harmony SASE, or your own custom configurations.
Administrators and IT managers can use our Internet Access policy to enforce organization security policies directly on endpoint devices to control the web traffic generated by each Member and device while managing the actual Rules, the Members on which they apply.
The Internet Access policy provides the ability to control Member or Member Groups' access to URLs and/or IP addresses based on predefined categories, custom URLs, used devices, time-based conditions, and more.
.png)
Access Policy
The Access Policy defines what users are allowed or denied access to when browsing the internet. It enables administrators to:
- Control access to web categories, for example, social media, news, gambling
- Allow or block specific URLs or domains
- Manage access to cloud-based and web applications, for example, Dropbox, YouTube, ChatGPT
These controls can be tailored per user or user group, ensuring policies are aligned with business roles and security requirements. For example, marketing teams might be granted access to social media platforms, while finance users are restricted to business-related sites only.
For Harmony SASE Linux clients, Secure Web Gateway (SWG) Access Policy rules do not support wildcard domain patterns (for example, *.example.com). Using wildcards may cause incorrect traffic evaluation or policy bypass. Use explicit domain names instead.
To view the Access Policy page, access the Harmony SASE Administrator Portal and click Internet Access > Access Policy.
| Column | Description |
|---|---|
| Name | Name of the Rule. |
| Action | Action for web traffic:
|
| Source |
|
| Destination | Destination of the web traffic generated by the source (Any, Web Categories, Custom URLs, or Applications). |
| Conditions | Allows admin to define time-based constraints for each rule. When a condition is applied, the rule is enforced only during the specified time frame (example: weekdays between 9:00 AM and 6:00 PM). This enables administrators to create policies that adapt to business hours, shift schedules, or specific access windows, for example, restricting access to social media sites outside of working hours. If no condition is set, the rule applies at all times. |
The end user needs to confirm the warning message, so it do not show the alert for the inspected resource for the next 24 hours.
Application Policy
Application Policy enables you to monitor, manage, and enforce access control over the SaaS applications used in an organization. It uses state of the art applications catalog and detection engine to accurately recognize and classify SaaS applications based on their behavior, signatures, and traffic patterns.
Support
Minimum agent version supported is 11.5.
Configuring Access Policy
To configure Access Policy, go to the Internet Access tab in the Harmony SASE Management Console platform:
- Go to Internet Access > Access Policy.Note - The access policy is a first-match-rule base.
- Add the relevant Access Policy by clicking on (+) Add New Rule:
- Name - Enter a name for the rule.
- Action - The type of Action that should be applied on the web traffic when the Rule is matched (Accept, Drop, or Warn).
- Drop - Web traffic is blocked.
- Accept- Web traffic is allowed.
- Warn - Web traffic is allowed, and an alert is triggered in the Monitoring Logs.
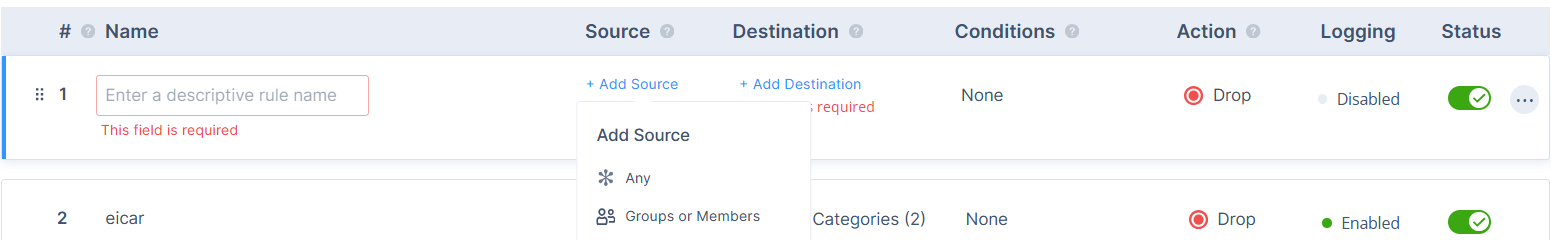
- Source- The specific Groups or Members to which the Access Policy Rule should be applied. Add user or group list to which you want to apply the rule.
- Click Add Source.
- Select Any or groups or members from the list.
- Click Apply.
- Destination - The destination of the web traffic generated by the Source (Web categories and/or Custom URLs and/or Applications). Select the destination.
- Click Add Destination.
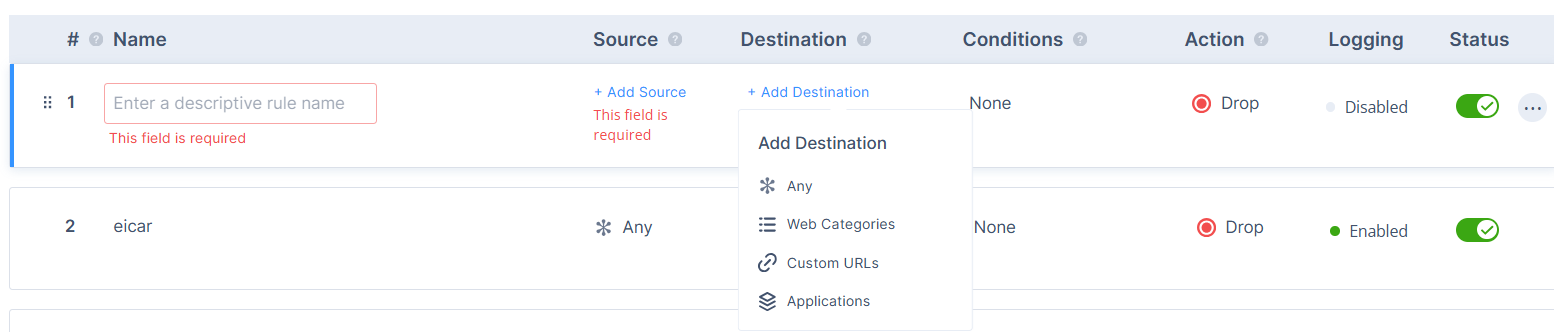
- To apply the rule to all destinations, select Any.
- Click Apply.
- To add web categories, select Web Categories.
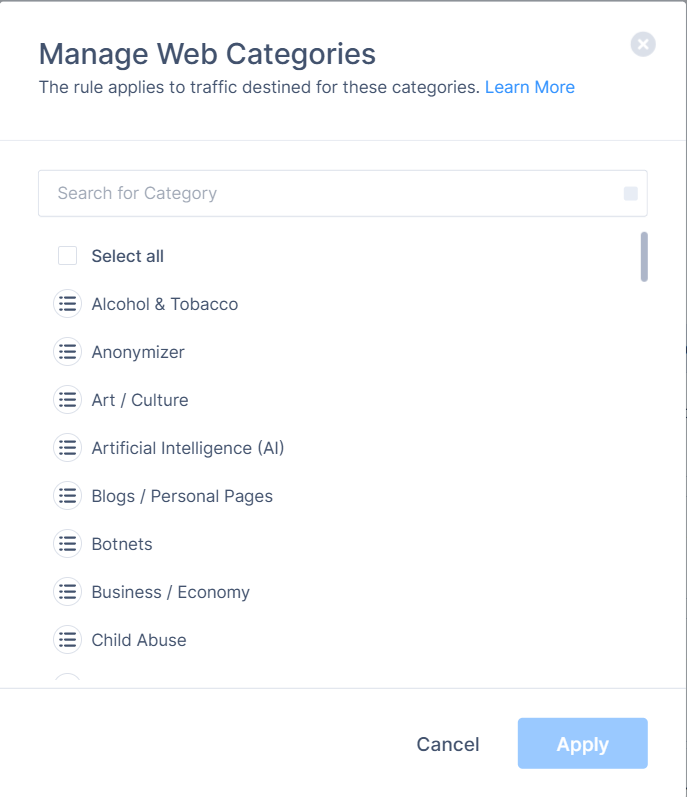 The Manage Web Categories window appears.
The Manage Web Categories window appears. - Select the categories from the list.
- Click Apply.
- To add custom URLs, select Custom URLs.
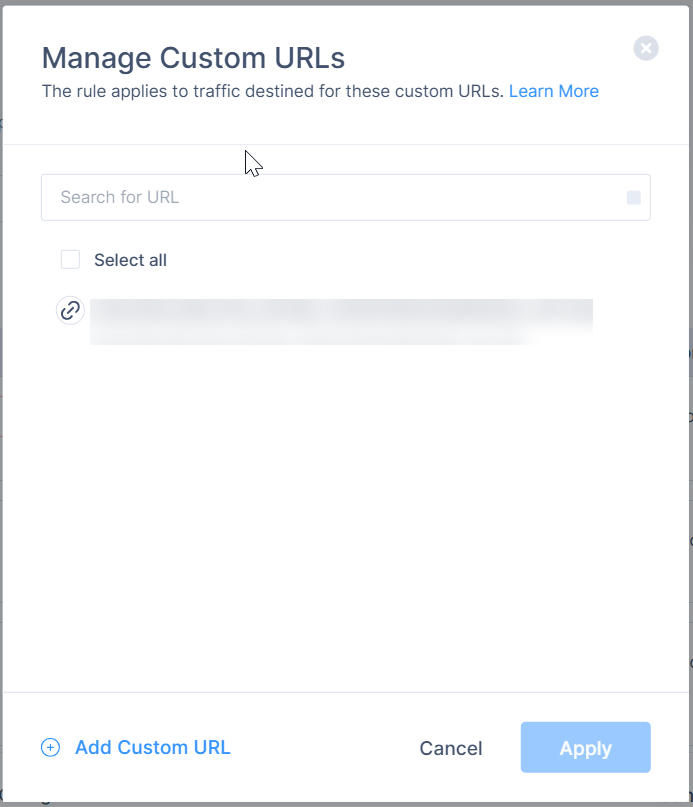 The Manage Custom URLs window appears.
The Manage Custom URLs window appears. - Select the custom URL. If the URL is not listed, click Add Custom URL and specify these and click Add URL:
- Name
- Description
- URL
Optionally, click Upload .CSV to upload a .csv file with list of URLs.
- Click Apply.
- To add Application, select Applications.
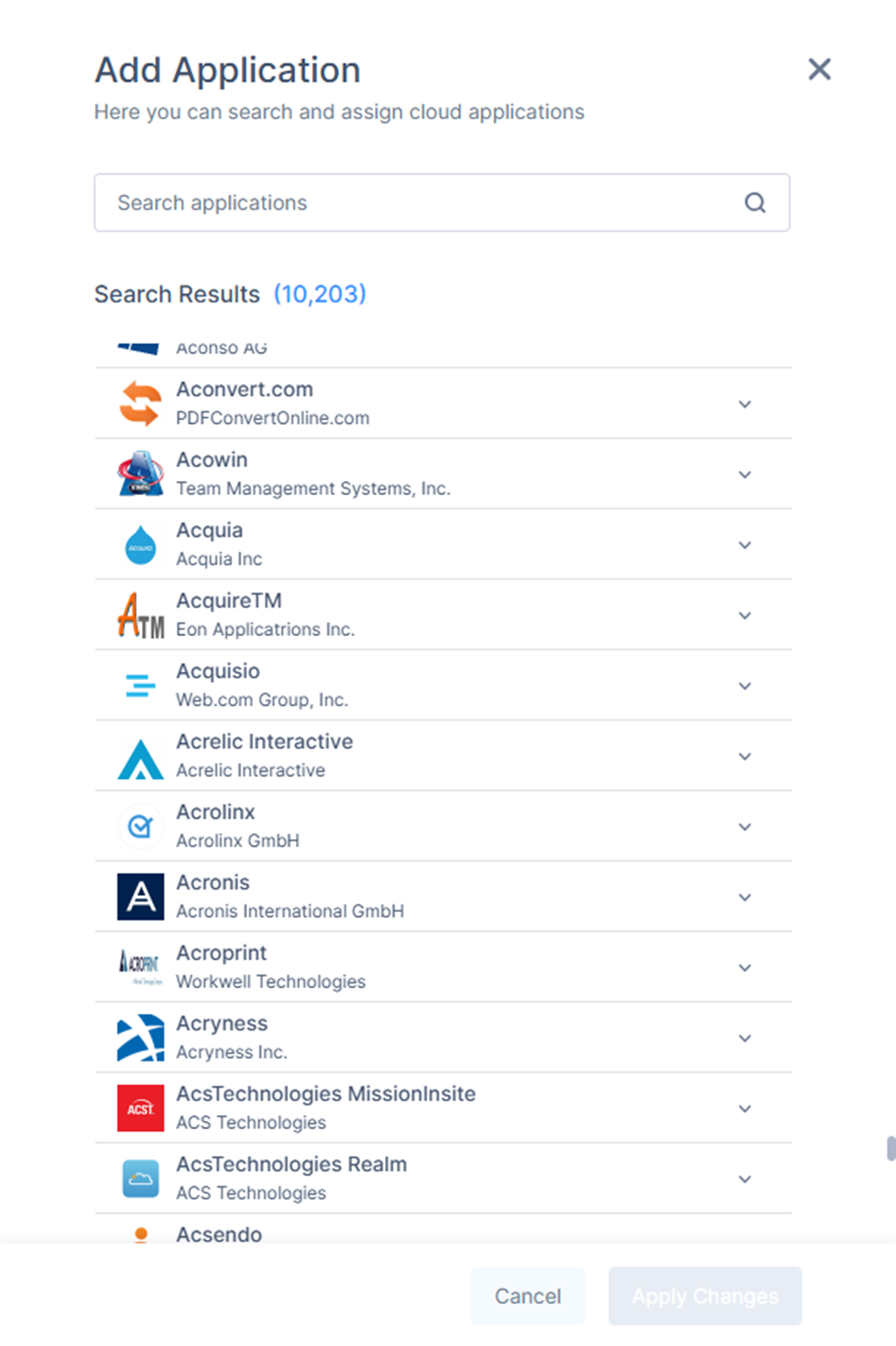 The Add Application window appears.
The Add Application window appears. - Search the application and click + to select the application.
- Click Apply Changes.
- Click Add Destination.
- Conditions - When the Access Policy should be enforced (Anytime / At specific days and times)
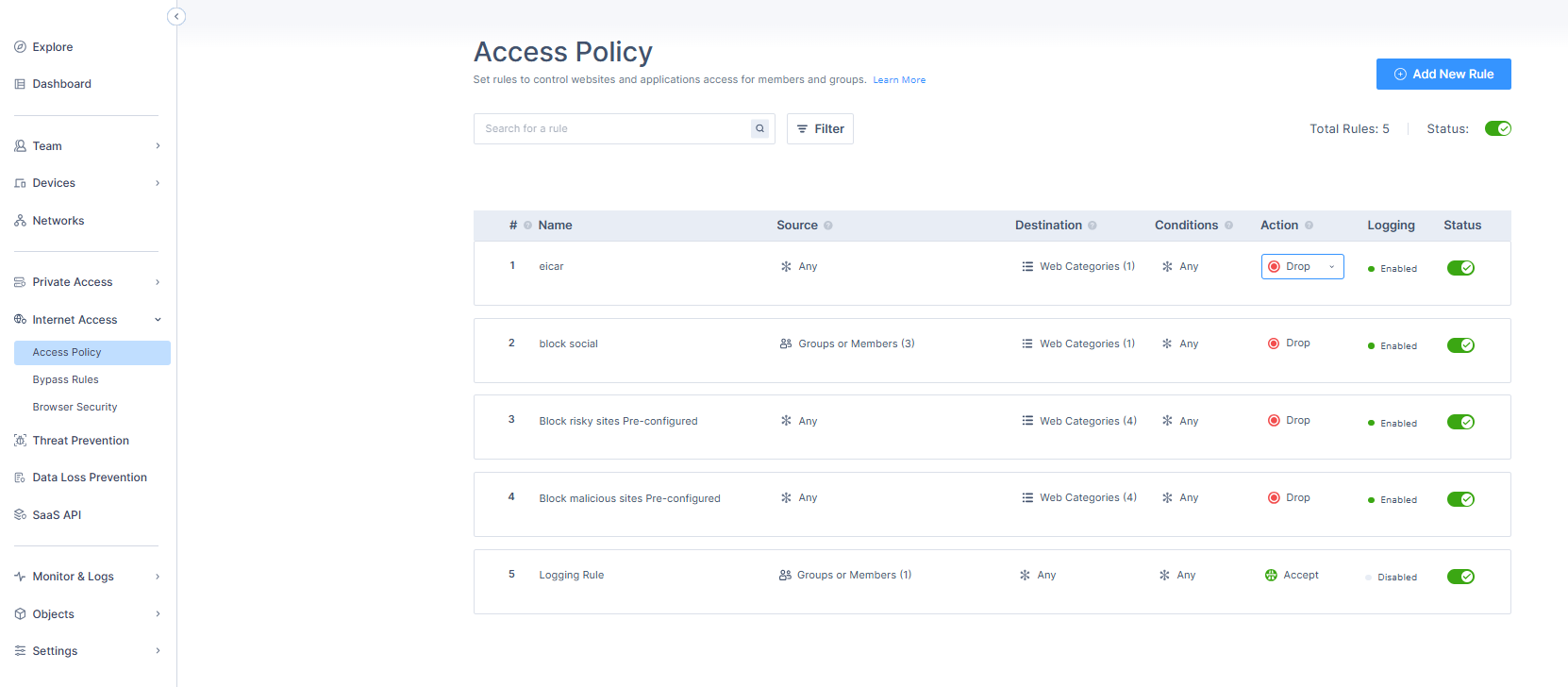
- Turn on the Status toggle button, to activate this rule.
- Once the Access Policy are defined, Click Apply.

- Click Apply.DisclaimerURLs containing protocols, queries, parameters, or anchors are not supported.
Tenant Restrictions
For more details, see Tenant Restrictions.
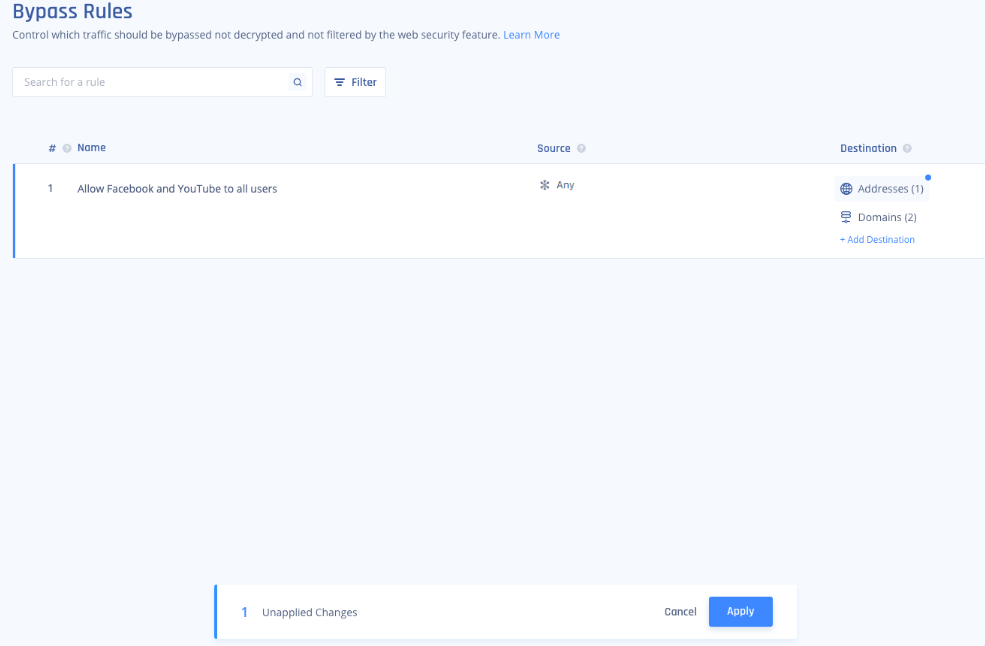
Bypass Rules
All Rules in the Bypass Rules section will override the rules defined in the Access Policy.
In other words, traffic that matches a Bypass Rule (i.e., sensitive data, private browsing, etc.) will not be inspected by Secure Web Gateway (SWG) and will be routed directly to its destination.
A vital component of the Bypass Rules is allowing web traffic for Groups or Members and specific OS processes running on the client device as they may experience the certificate pinning issue.
Configure Bypass Rules
- Navigate to Internet Access > Bypass Rules.
- Click on (+) Add New Rule
- Add the relevant Access Policy by clicking on (+) Add New Rule:
- Name - The name of the Rule to identify its purpose
- Source- The specific Group or a Member on whose web traffic the rule should be applied.Internet Access Bypass rulesIn the Bypass Rules section, you can define which Groups or Members are generating the web traffic and allow specific OS processes (such as Slack, Zoom, Teams, etc.) to bypass your Access Rule.
- Destination - The destination of the web traffic that is generated by the Source (Web Categories, Domains, and/or Custom URLs)
4. Once you've defined the Bypass Rules, Click on the blue Apply button at the bottom of the screen.
Bypass criteria
- Programs - Configure a specific program, application, or process name to be ignored by Access Policy.
- Web Categories - Choose from a list of predefined categories, which are updated daily.
- Domains - Configure specific domains which will be bypassed and not inspected by Access Policy.
Prioritizing Rules
All Access Policy and Bypass Rules are prioritized based on order (#1 being the top priority). All web traffic packets are checked against the Rules in a top-down approach until matched (i.e., once the inspected packet is matched to a Rule, it's not being verified against Rules with a lower priority).
The Access Policy Rule Default Action (if no rule is defined) is set to Accept.
Changing Rule Prioritization
Changing Rule Prioritization
1. Navigate to Internet Access -> Access Policy / Bypass Rules
2. Drag the right-hand side of the desired Rule up or down to change its prioritization.
3. Once you've defined the Rules priorities, click the blue Apply button at the bottom of the screen.
Troubleshooting
If you encounter issues during or after the setup, try reviewing your settings to ensure everything matches the instructions. In particular, check the IP addresses and other details you entered during setup. If issues persist, please consult our dedicated support.
Support Contacts
If you have any difficulties or questions, don't hesitate to contact Harmony SASE's support team. We offer 24/7 chat support on our website at Perimeter81.com, or you can email us at sase-support@checkpoint.com. We're here to assist you and ensure your VPN tunnel setup is a success