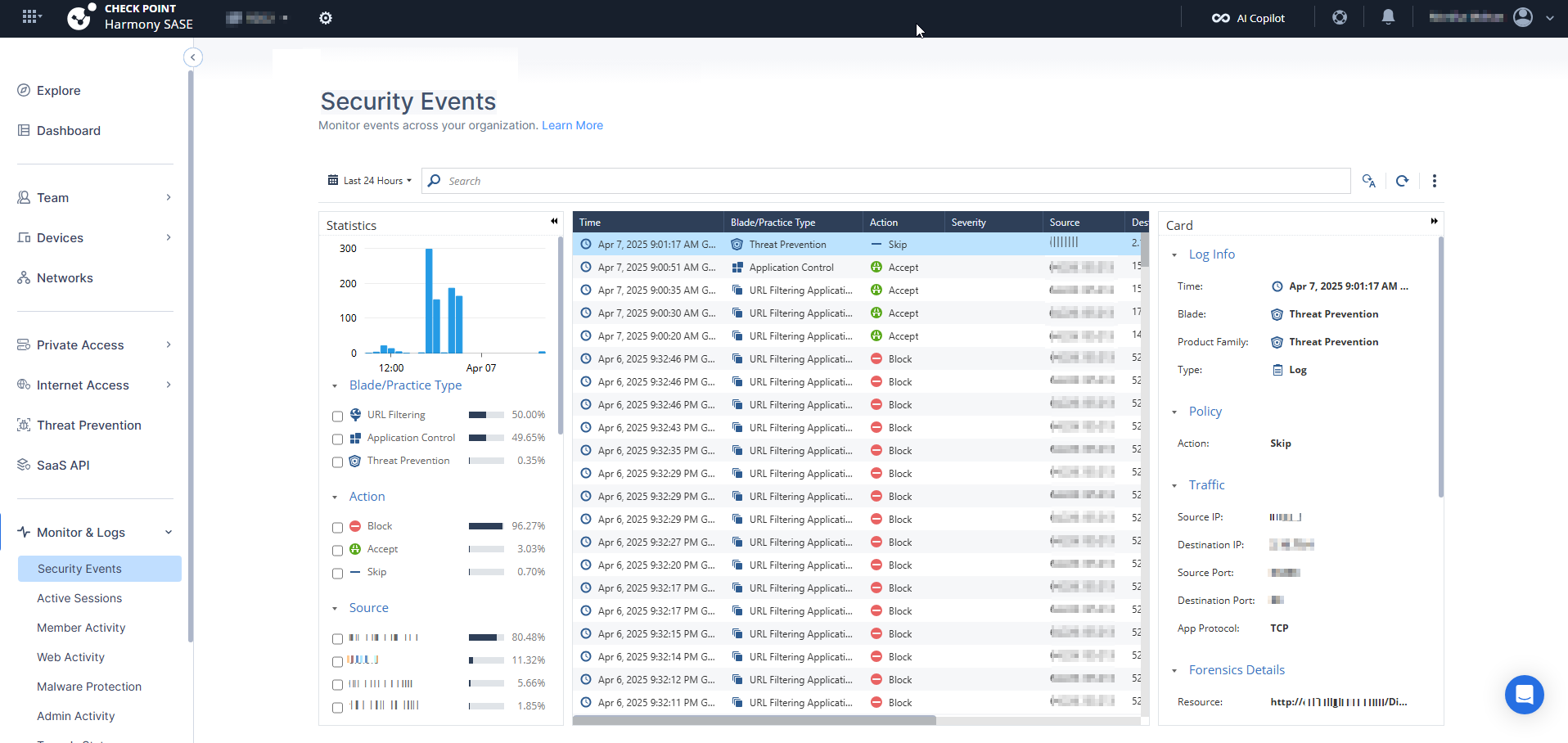
The Security Events provides an integrated view of security logs directly within the Harmony SASE platform. It allows easy monitoring, searching, and filtering of Harmony SASE related security events.
To view the Security Events page, access Harmony SASE and go to Monitor & Logs > Security Events.
Notes:
- The Security Events limit the number of events to 300 per search.
- You can also search for additional parameters that do not appear as quick filters.
For example:- The URL resource using resource:"https://go.microsoft.com/fwlink/"
- The Destination Port by using dst_port: 443
- The Source Port by using src_port:55321
- The Device name using device_name: "DESKTOP-123"
.png)
Supported Events
The Security Events supports these event types:
- URL Filtering and Application Control
- Threat Emulation
- Malware Protection
- Anti-Bot
- Firewall Events
Statistics
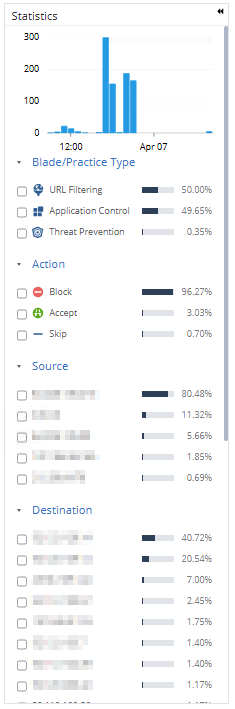
The Statistics panel provides a visual summary including these:
- Event distribution by Blade Type
- Breakdown by Actions
- Accept
- Block
- Detect
- Skip
- Source IP distribution
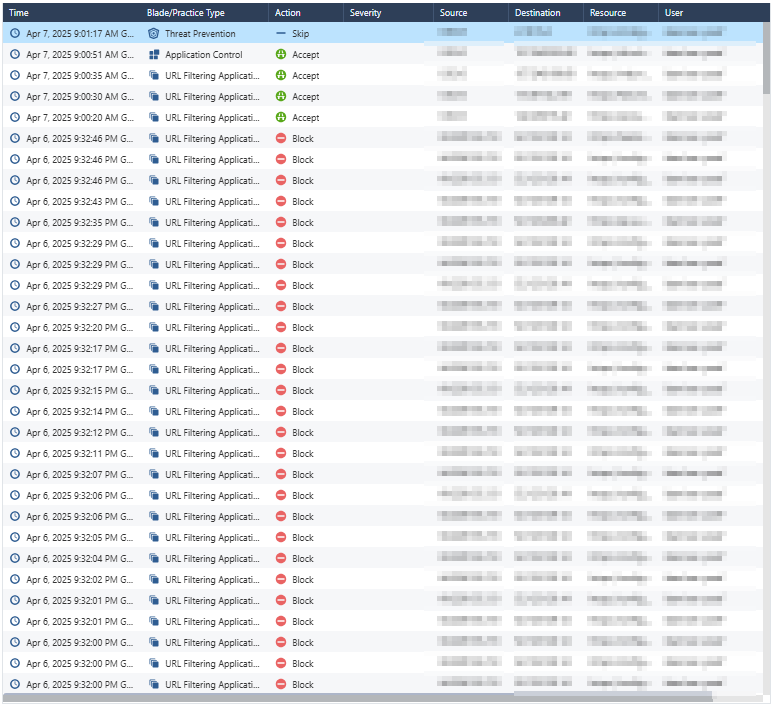
Logs
| Column | Description |
|---|---|
| Time | Timestamp when the event occurred. |
| Blade/Practice Type | Specific security module responsible for the event, for example, URL Filtering and Malware Protection. |
| Action | Security action taken:
|
| Severity | Severity level of the event. |
| Source/Destination IP | Network endpoints involved. |
| Resource | URL or resource accessed. |
| User | User name. |
Card
You can click on a specific log entry to open a detailed log card, which provides:
- Complete event description.
- Session details, such as ports, URLs, downloaded data and so on.
The card offers an in-depth view for thorough analysis.
.PNG)