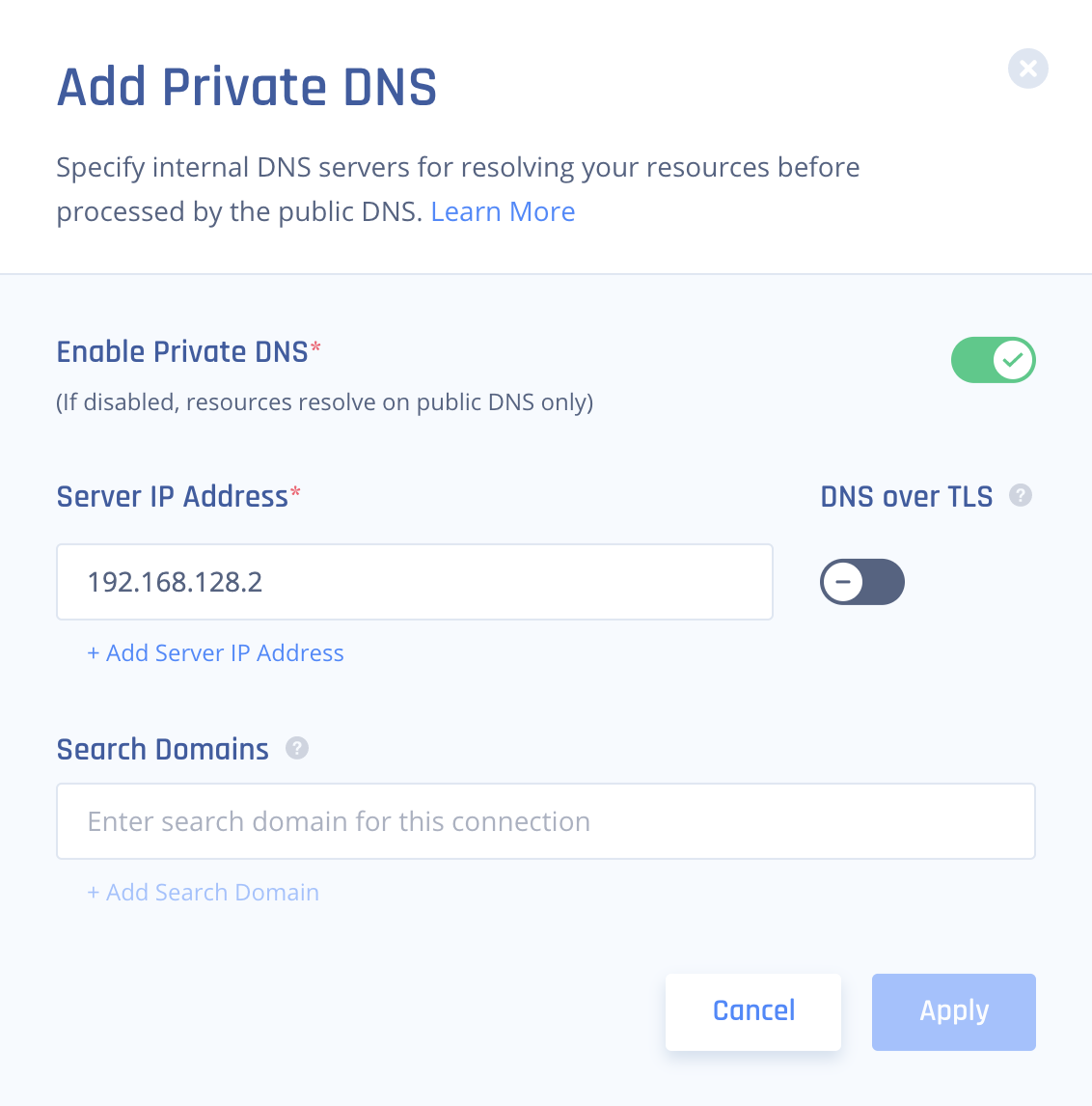
If you are utilizing the Private Zone/Private DNS feature of Google Cloud, you can utilize the those name servers via private IP's through the tunnel established on the Harmony SASEimeter81 gateway. You can take full advantange of private DNS zones and still resolve external records. You can enable Private DNS after enabling the following changes in Google Cloud Platform.
Some prerequesities for this guide:
- GCP project
- VPC Network - This can be created or you can use Google predefined list of subnets
- Site to Site VPN tunnel to the VPC from Harmony SASE (Tunnel)
This process will allow the administrator to expose Google's Cloud DNS via a private IP inside one or multiple networks that you have defined in your VPC.
via GUI/Web
Navigate to Network Services -> Cloud DNS
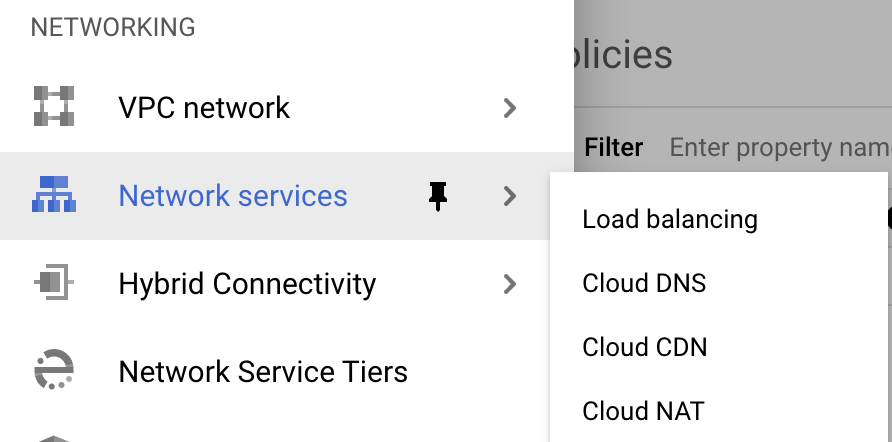
Navigate to DNS Server Policies
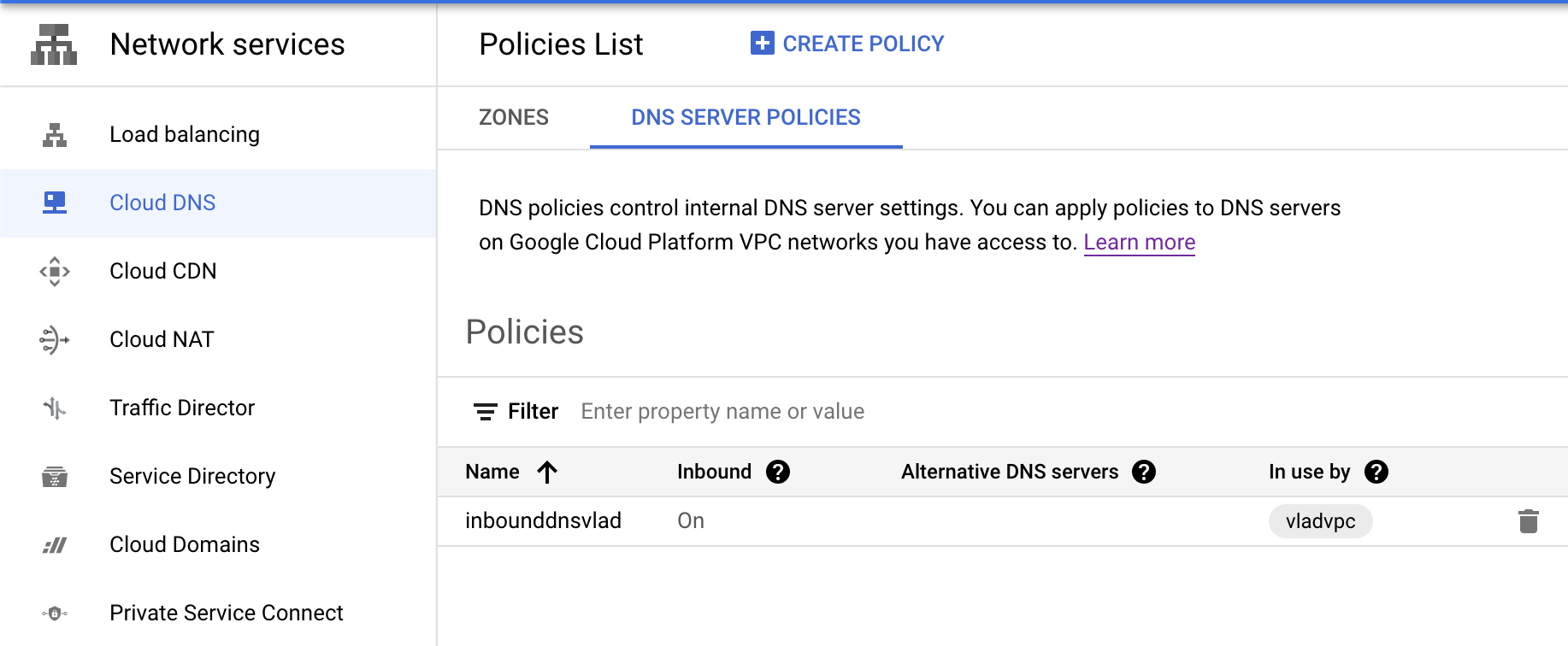
Create a DNS Server Policy
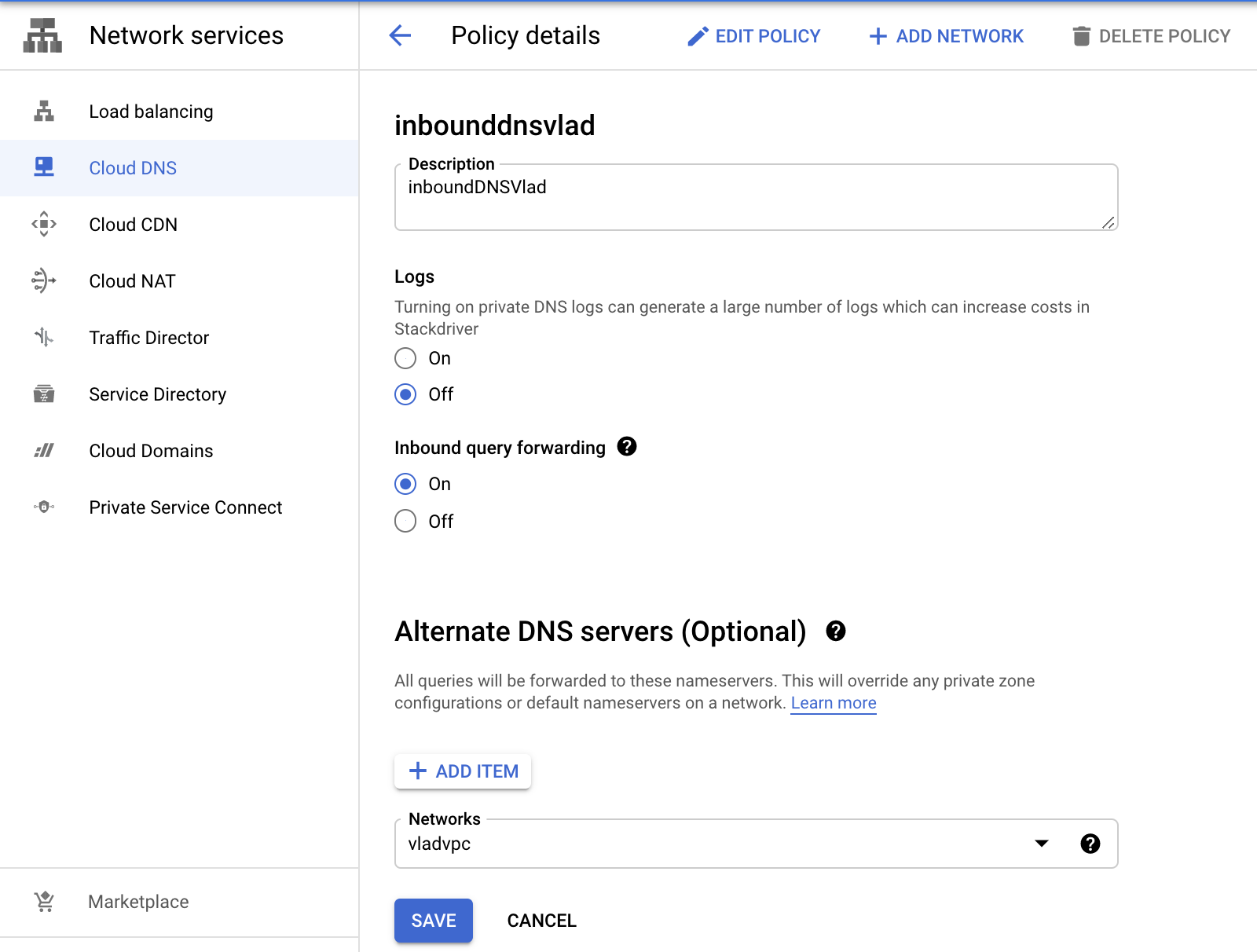
Make sure that inbound query forwarding is On and all of the desired networks are selected.
You will get an IP address from the top of the network the policy is used by: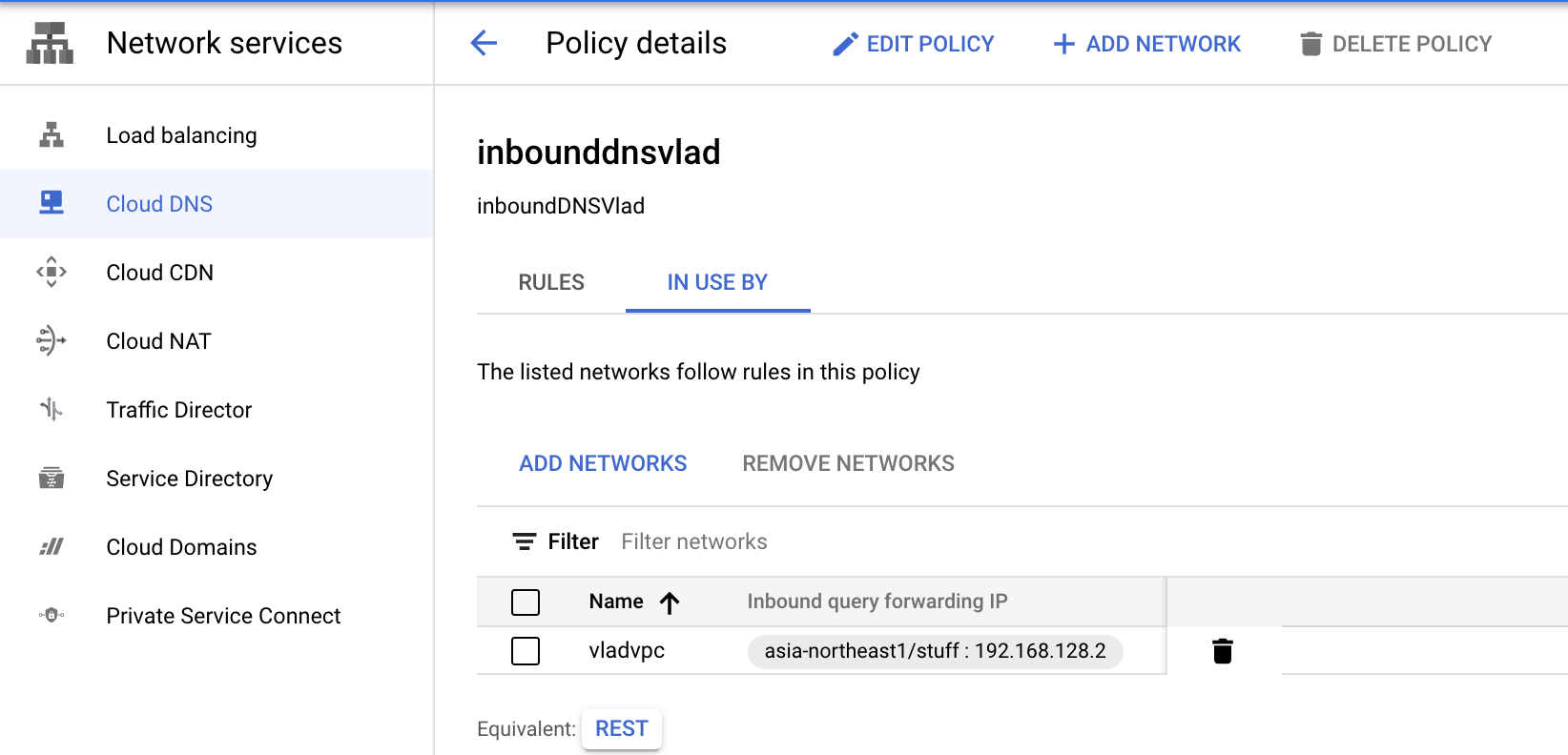
This is the private IP that you can use for Private DNS setup in Harmony SASE.
You can add more networks here if you like but please make sure that routing is available for those so that Harmony SASE can reach them via CLI.
- Install Google Cloud SDK (https://cloud.google.com/sdk/docs/install)
- Authenticate/Initialize your gcloud cli environment
gcloud auth login
- Create an inbound server policy for DNS
gcloud dns policies create {{NAME}} --description={{DESCRIPTION}} --networks={{VPC_NETWORK_LIST}} --enable-inbound-forwarding
{{NAME}} - name for the policy.
{{DESCRIPTION}} - Description of the policy.
{{VPC_NETWORK_LIST}} - Comma separated list of VPC networks (not subnets)
ops-vlad:~ vbekker$ gcloud dns policies create inbounddnsvlad --description=inboundDNSVlad --networks=vladvpc --enable-inbound-forwarding
Created Policy [https://dns.googleapis.com/dns/v1/projects/vladgcp/policies/inbounddnsvlad].
{
"description": "inboundDNSVlad",
"enableInboundForwarding": true,
"enableLogging": false,
"id": "8199820556025819315",
"kind": "dns#policy",
"name": "inbounddnsvlad",
"networks": [
{
"kind": "dns#policyNetwork",
"networkUrl": "https://compute.googleapis.com/compute/v1/projects/vladgcp/global/networks/vladvpc"
}
]
}
Validation
Here is a succesfull DNS lookup from the gateway directly to the server and also to our dns forwarder
Directly querying the name server
vlad@vodFpGngx3:~$ dig www.vpcdnszone.com @192.168.128.2
; <<>> DiG 9.11.3-1ubuntu1.13-Ubuntu <<>> www.vpcdnszone.com @192.168.128.2
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 51251
;; flags: qr aa rd; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; WARNING: recursion requested but not available
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 512
;; QUESTION SECTION:
;www.vpcdnszone.com. IN A
;; ANSWER SECTION:
www.vpcdnszone.com. 300 IN A 192.168.128.50
;; Query time: 161 msec
;; SERVER: 192.168.128.2#53(192.168.128.2)
;; WHEN: Fri Mar 05 00:11:01 UTC 2021
;; MSG SIZE rcvd: 63
Via local forwarder
vlad@vodFpGngx3:~$ dig www.vpcdnszone.com
; <<>> DiG 9.11.3-1ubuntu1.13-Ubuntu <<>> www.vpcdnszone.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 46053
;; flags: qr aa rd; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 0
;; WARNING: recursion requested but not available
;; QUESTION SECTION:
;www.vpcdnszone.com. IN A
;; ANSWER SECTION:
www.vpcdnszone.com. 300 IN A 192.168.128.50
;; Query time: 156 msec
;; SERVER: 127.0.0.1#53(127.0.0.1)
;; WHEN: Fri Mar 05 01:38:15 UTC 2021
;; MSG SIZE rcvd: 70
Finally, enable Private DNS on the network: