Many of you may have instances and VPC's in AWS and you are very likely utilizing AWS's Route53 DNS infrastructure. In addition to public domain zone management, AWS offers to expose certain zones via private IP access. The proper term for this is inbound and outbound endpoints. We'll be focusing on inbound endpoints in order to better architect Harmony SASE's Private DNS feature into your network.
It is considered a good network security practice to make sure that internal resources for your organization's prod or perhaps dev environment are permitted access via a private subnet, making sure that valuable resources aren't on the public internet even if you have security rules in place. Managing a list of public IP's is sure to inflate the more complexity and more people you have.
Accessing internal resources by name is a huge benefit for any environment. There are always a handful set of tools that you may not want to expose to the public.
If you've spun up a tunnel from Harmony SASE to AWS using Site to Site, then we need to spin up Inbound Endpoints and create a security group allowing requests on port 53
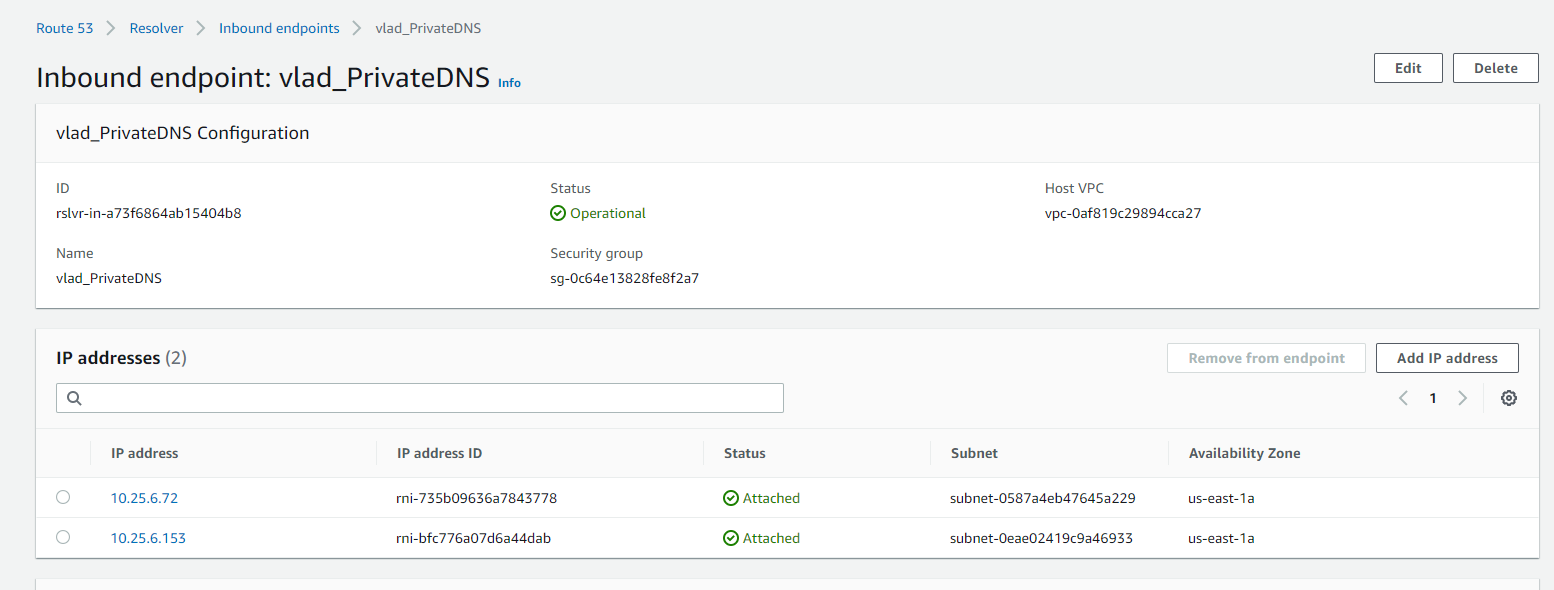
Navigate to** Route 53 > Resolver > Inbound endpoints**
Create a new resolver: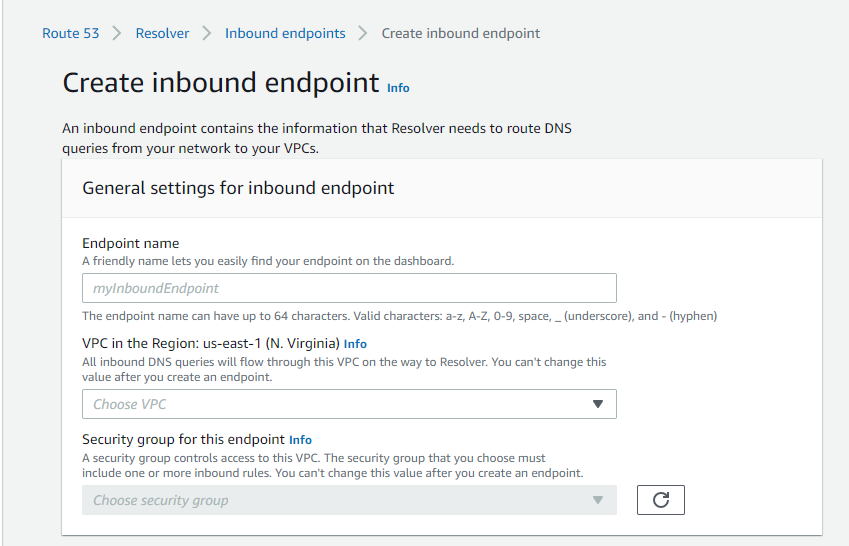
You should now have a resolver for each of the subnets you've selected. The resolvers will be in the form of IP addresses that you are able to configure within Harmony SASE's Private DNS feature