Introduction
Welcome to our guide on establishing a Site-to-Site VPN tunnel between your Harmony SASE network and the WatchGuard Firebox environment.
Breakdown of topics
- Pre-requisites
- Configuration Steps
- Verifying the Setup
- Troubleshooting
- Support Contacts
Pre-requisites
To successfully follow this guide, ensure that:
- Have an active Harmony SASE account and an established network.
- Have the Harmony SASE application installed on your devices.
- Possess an active WatchGuard Firebox setup with the necessary administrative rights.
Configuration Steps
Configuring an IPSec tunnel in the Management Platform
- Under Network in the Management Platform on the left side, select the name of the network in which you'd like to set the tunnel.
- Locate the desired gateway, and select the three-dotted menu (...).
- Select Add Tunnel and then IPSec Site-2-Site Tunnel.
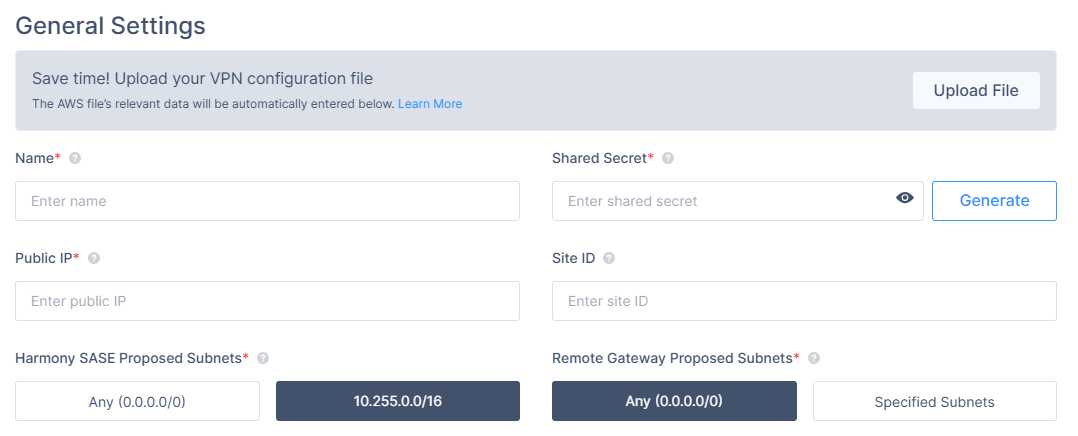
- In the General Settings section, specify these:
- Name: Choose whatever name you find suitable for the tunnel.
- Shared Secret: Insert a string of your own or use Generate.
- Public IP: Insert the public IP of the firewall (you can copy it from the Fireware Web UI URL).
- Remote IP: Insert the public IP of the firewall (same address as above).
- Harmony SASE Gateway Proposal Subnets: By default, this should be set to 10.255.0.0/16.
- Remote Gateway Proposal Subnets: 0.0.0.0/0 or specify according to your customized settings.
- In the Advanced Settings section, specify these:
- IKE Version: V2 if the Firewall version supports it, V1 otherwise.
- IKE Lifetime: 8h
- Tunnel Lifetime: 1h
- Dead Peer Detection Delay: 10s
- Dead Peer Detection Timeout: 30s
- Phase 1:
- Encryption (Phase 1): aes256
- Integrity (Phase 1): sha256
- Key Exchange Method: modp2048
- Phase 2:
- Encryption (Phase 2): aes256
- Integrity (Phase 2): sha256
- Key Exchange Method: modp2048
Leave the rest of the fields with the default values (as shown in the image).
Configuring the tunnel in the WatchGuard Management Interface
- Open Fireware Web UI.
- In the left panel, select VPN, then BOVPN Virtual Interfaces.
- Select ADD
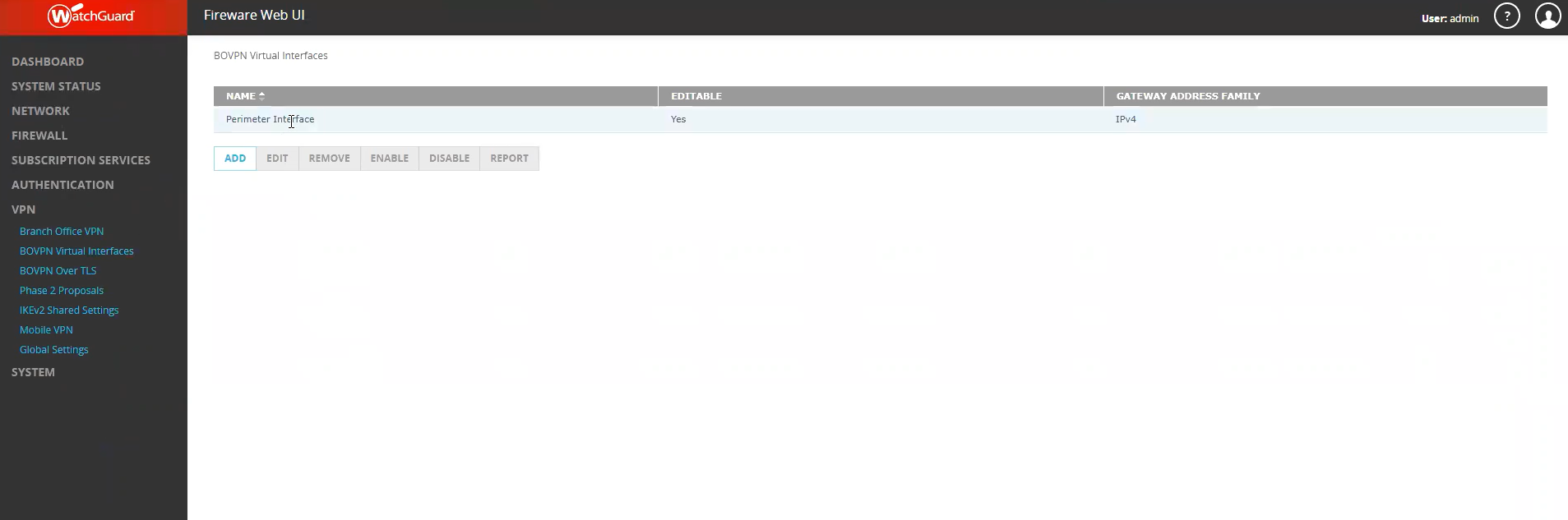
- Select 'Cloud VPN or Third-Party Gateway' under Remote Endpoint Type.
- Select 'IPv4 Addresses' under Gateway Address Family.
- Under 'Gateway Settings' fill in the Shared Secret you created on the Harmony SASE Platform.
- Local Gateway
- External Interface: External
- Interface IPAddress: Primary Interface IP Address.
- Remote Gateway
- Select Static IP Address and enter your gateway IP.
- Select By IP Address and enter your gateway IP.
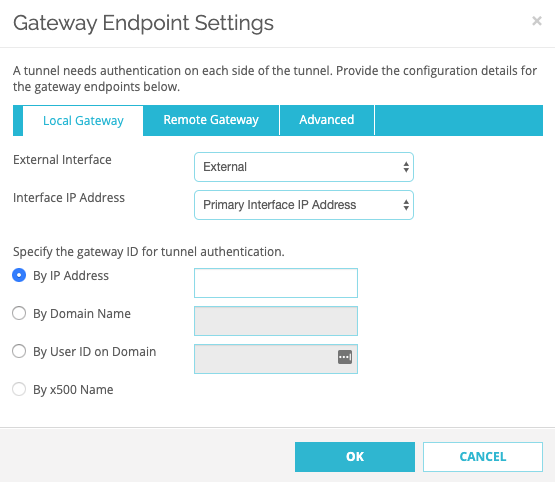
- Advanced
- Select "Specify a different pre-shared key for each gateway endpoint" and enter the Shared Secret.
- Leave the rest of the fields with the default values.
- Local Gateway
- Go to the Phase 1 Settings tab and fill in the following information:
- Version:IKEv2 if the Firewall version supports it, IKEv1 otherwise.
- Mode: Main
- NAT Traversal: Check
- Keep-alive Interval: 20 seconds
- IKE Keep-alive: Check
- Message Interval: 30 seconds
- Max failures: 5
- Dead Peer Detection (RFC3706): Check
- Traffic idle timeout: 20 seconds
- Max retries: 5
- Go to Transform Settings and select ADD. Fill in the following information:
- Authentication: SHA2-256
- Encryption: AES(256-bit)
- SA Life: 8 hours
- Key Group: Diffie-Hellman Group 14
- Go back to the BOVPN Virtual Interfaces page.
- Click the VPN Routes tab and select Add.
.png) The VPN Route Settings window appears.
The VPN Route Settings window appears.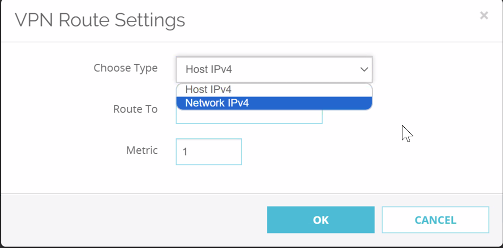
- From the Choose Type list, select Network IPv4.
- In the Route To field, enter the network IPv4 or the customized subnet you entered while creating your Harmony SASE network. The default value is 10.255.0.0/16.
- Leave the Metric field with default value 1.
- Go to Phase 2 Settings.
- Click the checkbox next to Enable Perfect Forward Secrecy and select Diffie-Hellman Group 14.
- Under IPSec Proposals, choose ESP-AES256-SHA256, then select ADD.
- Select Save (leave the settings in the Multicast Settings tab alone).
Validating the tunnel is up
- At the Fireware Web UI, go to System Status -> VPN Statistics --> Branch Office VPN. If the tunnel is active, the line will appear in the table as shown below:

If you experience a different result, carefully go through all the steps; however, if the issue persists, please contact our support team.
Verifying the Setup
After following the above steps, your tunnel should be active.
To verify, go to your Harmony SASE dashboard, locate the tunnel you just created, and check the tunnel status.
It should indicate that the tunnel is "Up", signifying a successful connection.
Next, connect to your network using the Harmony SASE agent and attempt to access one of the resources in your environment.
Troubleshooting
If you encounter issues during or after the setup, try reviewing your settings to ensure everything matches the instructions. In particular, check the IP addresses and other details you entered during setup. If issues persist, please consult our dedicated support.
Support Contacts
If you have any difficulties or questions, don't hesitate to contact Harmony SASE's support team. We offer 24/7 chat support on our website at sase.checkpoint.com, or you can email us at sase-support@checkpoint.com. We're here to assist you and ensure your VPN tunnel setup is a success.
.PNG)