This article describes how to ensure that several sites and cloud resources are connected securely using the Harmony SASE Platform.
If the two sites are both tunneled to your Harmony SASE network, you can enable the two to communicate via the Harmony SASE network so that both sites will have a full and secure line between them without the need for a Harmony SASE client.
IPSec based connections
Ensure both tunnels are route-based tunnels; that is, they do not depend on a specific internal subnet to create a handshake between the sites, but a route is configured on each device’s separate Route Table indicating which subnets to forward into the tunnel.
On the Harmony SASE Management Platform, set both tunnel’s “Harmony SASE Gateway Proposal Subnets” and “Remote gateway Proposal Subnets” to ANY (0.0.0.0/0).
This may make the tunnel go down! Please make sure the device you are using supports route-based VPN. This means the tunnel is set up to 0.0.0.0/0 and a route is added separately..png)
Make sure the Routes Table on the Harmony SASE side has all of the routes of all of the sites configured (Network/ Route Tables) so in case you had them defined within the tunnel module, instead you need to add them here.
.png)
Click Add Route and add the routing to the internal LAN subnets that are behind each tunnel.
.png)
After you are done, click Apply Configuration.
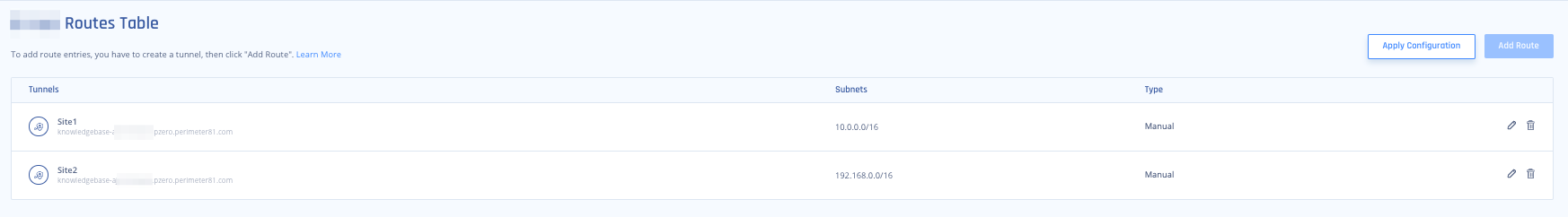
- Go to the first site's routing table (Site1), and in addition to the route that indicates all Harmony SASE subnets (usually 10.255.0.0/16) to go through the Site to site tunnel, add a route dictating all traffic that goes to the second site's LAN subnet as well.
- Go to the second site's routing table (Site2), and set up a static route indicating both the Harmony SASE LAN Subnet AND Site1’s LAN subnet to go through the IPSEC Site-2-Site tunnel.
- Go to the first site's routing table (Site1), and ensure that there are two Phase II tunnels
- One from Site1's internal subnet <==> to Harmony SASE's Subnet
- Another from Site1's internal subnet <==> to Site2's internal subnet.
- The reverse should be configured in Site2's Phase II IPSEC Proposal as well.
- One from Site2's internal subnet <==> to Harmony SASE's Subnet
- Another from Site2's internal subnet <==> to Site1's internal subnet
WireGuard based connections
1. In order to establish a connection from one resource to another, you'll need to reinstall the connector, as the default installation (Accessor mode) does not allow it.
Ubuntu
# Locate the WireGuard packages (the output of this command is the full package name)
dpkg -l | grep wireguard
# Delete all packages found that are associated with WireGuard (replace pkg with the output from the previous command)
apt-get remove --purge pkg# Locate the WireGuard packages (the output of this command is the full package name)
yum list installed | grep wireguard
# Delete all packages found that are associated with WireGuard (replace pkg with the output from the previous command)
yum remove pkg2. Once you successfully removed the files mentioned in the commands above, reboot the machine and execute the connector installation script (the curl command that you copied from the Management Platform).
3. When you reach the 4th step, choose NO (n), which will prevent accessor mode installation.
4. Proceed with the installation.
5. The script will ask "Do you want to route whole traffic through connector tunnel? [y/N]"
- Select No → This will make sure that the default route for the Linux machine doesn't get modified.
- Select Yes → This will override the default route on the machine, forwarding all traffic via the Wireagurd connection.
- Afterward, ensure that the Router/Firewall on the network sends all of the route's traffic(0.0.0.0/0) via the internal IP of the Wireguard connector. If the Linux machine IS the router, instructions can be found below.
6. Do you want to enable IP forwarding (router mode)? [y/N]
- If the Linux server is acting as a firewall, router, or NAT device → Select Yes.
- Select No → In case another device has the "Router" role in the network.
7. Open the Route table of the network in which the WireGuard connector is installed (usually your router or firewall).
8. Configure a static route dictating all traffic from your Harmony SASE LAN subnet (10.XXX.0.0/16) and your other desired remote subnet to go through the IP of the machine that hosts the connector.
Open the terminal of the Linux machine that hosts the connector and execute the following command:
# Temporarily shut the connector down
wg-quick down wg0
# Open the connector's route table.
vi /etc/wireguard/wg0.conf
# Enter the subnets of the resources you'd like to communicate with each other
set AllowedIPs = <Harmony SASE Subnet>, <Site1 Subnet>,< Site 2 Subnet>
# Turn the connector up
wg-quick up wg0
# Make sure that the desired change has taken place
wg show
To disable source/destination checking
1. Open the Amazon EC2 console at https://console.aws.amazon.com/ec2/.
2. In the navigation pane, choose Instances.
3. Select the relevant instance.
4. Choose Actions, Networking, Change source/destination check.
5. For Source/destination checking, select Stop.
6. Choose Save.
7. If the instance has a secondary network interface, choose it from Network interfaces on the Networking tab. Choose the interface ID to go to the network interfaces page. Choose Actions, Change source/dest. check, clear Enable, and choose Save.