Understanding Zero-Trust Application?
Harmony SASE's Application Access feature secures your users' access to privately owned resources via their web browser without a need to install any VPN software on the computer.
Requirements
You would first need to spin up a Harmony SASE private network and make sure that this network has an IPSEC Tunnel or a Wireguard connector which will allow communication with the internal host that you wish to secure.
- Securing access to publicly accessible websites or SaaS providers (Such as Microsoft Office 365 or Gmail) is not supported using Harmony SASE's Zero Trust Application Access.
- In order to secure access to such public websites - the Harmony SASE Agent might be a better fit.
How to Manage Zero Trust Applications
To get started, you’ll need to add an application to your Harmony SASE account. Next, you will need to configure the application by filling out the General Settings form. Also, you will have the option to choose which groups of users will have access to the application and which policy will be included.
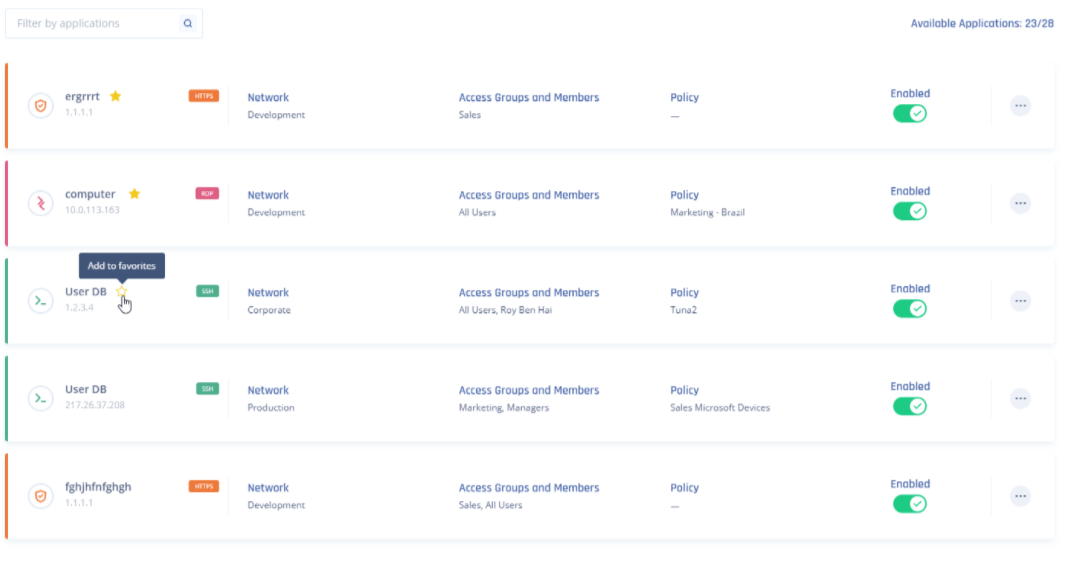
Now, a list of the applications that you have deployed will be available. To change the application permissions access, select the application setting option. Now you will have full control of the application’s settings including rules of access.
For each policy, you can set up customized rules for users' access. The identification rules can be based on network, device, location, work schedule, and connection time. If the user's identification and policy rules match up, you will have access to the application deployed on the network.
Each user will see a complete list of available applications that you have permission to access. Once you select the application you will be automatically connected and will be able to work securely.
After you have created an application, a list of the applications that you deployed will be available. You will be able to switch which group of users will have access and which policy will be enabled for the application. If the user's identification and policy rules match up, they will have access to the application deployed on the network.
Each user will see a complete list of available applications that they have permission to access.
Once they select the application they will be automatically connected and will be able to work more securely.
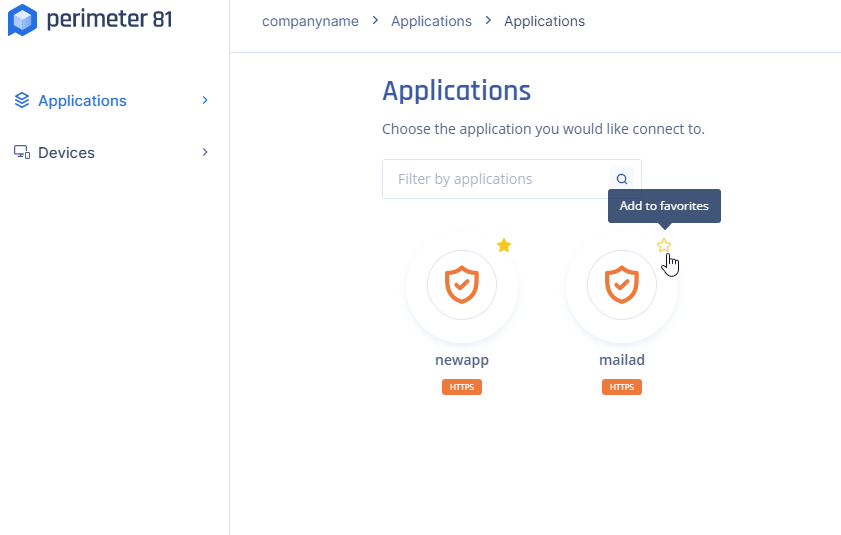
Favorites
Favorite applications will appear first in the list and are retained across different browsers and devices for the same user.
Recommendations
- Regularly review who has access to what resources.
- Use strong authentication mechanisms.
Troubleshooting
If you encounter issues during or after the setup, try reviewing your settings to ensure everything matches the instructions. In particular, check the IP addresses and other details you entered during setup. If issues persist, please consult our dedicated support.
Support Contacts
If you have any difficulties or questions, don't hesitate to contact Harmony SASE's support team. We offer 24/7 chat support on our website at sase.checkpoint.com, or you can email us at sase-support@checkpoint.com. We're here to assist you and ensure your VPN tunnel setup is a success
Supported Protocols
Specific articles on how to configure your Application Access per the desired protocol you wish to secure:
- How to add an SSH application
- How to add an HTTPS application
- How to add an HTTP application
- How to add an RDP application
- How to add a VNC application