Understanding Generic SAML
This article describes how Harmony SASE allows users to authenticate against an external IdP using the Security Assertion Markup Language (SAML) protocol.
The platform can automatically manage the IdP added Members and assign them to IdP correlating Groups.
SAML-based federation involves two parties:
An identity provider (IdP): authenticates users and provides to Service Providers an Authentication Assertion if successful.
A service provider (SP): relies on the Identity Provider to authenticate users.
Harmony SASE supports the SAML protocol and can serve as the service provider for users that are authenticated by different IdPs.
During the login process, Members will be redirected to the IdP in order to authenticate.
Once the user is authenticated, Harmony SASE will get a SAML assertion and associate the Member with the appropriate role and policies.
How to integrate with a SAML IdP
In order to integrate with a SAML IdP, you will need to create a dedicated Harmony SASE Application within your SAML IdP.
Most of the IdPs will require the following information when creating a new application:
- Single sign-on URL:
- For US based platform: https://auth.perimeter81.com/login/callback?connection={{WORKSPACE}}-oc
- For EU based platform: https://auth.eu.sase.checkpoint.com/login/callback?connection={{WORKSPACE}}-oc
- For AU based platform: https://auth.au.sase.checkpoint.com/login/callback?connection={{WORKSPACE}}-oc
- For IN based platform: https://auth.in.sase.checkpoint.com/login/callback?connection={{WORKSPACE}}-oc
- Audience URI (SP Entity ID):
- For US based platform: urn:auth0:perimeter81:{{WORKSPACE}}-oc
- For EU based platform: urn:auth0:eu-sase-checkpoint:{{WORKSPACE}}-oc
- For AU based platform: urn:auth0:qsase-au:{{WORKSPACE}}-oc
- For IN based platform: urn:auth0:qsase-in:{{WORKSPACE}}-oc
Remember to replace {{WORKSPACE}} with your actual workspace name
In order to map the IdP members correctly the following attributes have to be passed to the platform:
| IdP Attribute | Harmony SASE Mapping |
|---|---|
| Email Address | |
| First Name | given_name |
| Last Name | family_name |
Should you require to pass group memberships to Harmony SASE:
| IdP Object | Harmony SASE Mapping |
|---|---|
| Groups | groups |
Once the application is created you'll be provided with the following information:
- X.509 Certificate
- IdP Sign-in URL
Configuring Harmony SASE
You need to configure the integration from the Harmony SASE side.
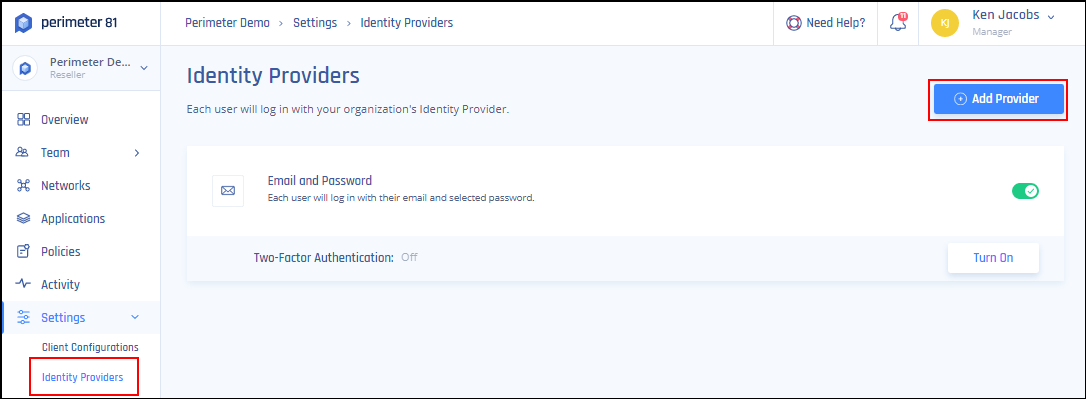
- Log in to your Harmony SASE Management Platform, and navigate to Settings and then Identity Providers.
- Select + Add Provider.
- Select SAML 2.0 Identity Cloud.
- Fill in the Sign In URL provided by the IdP.
- Add your organization domains.
- Paste the X.509 Certificate provided by the IdP.
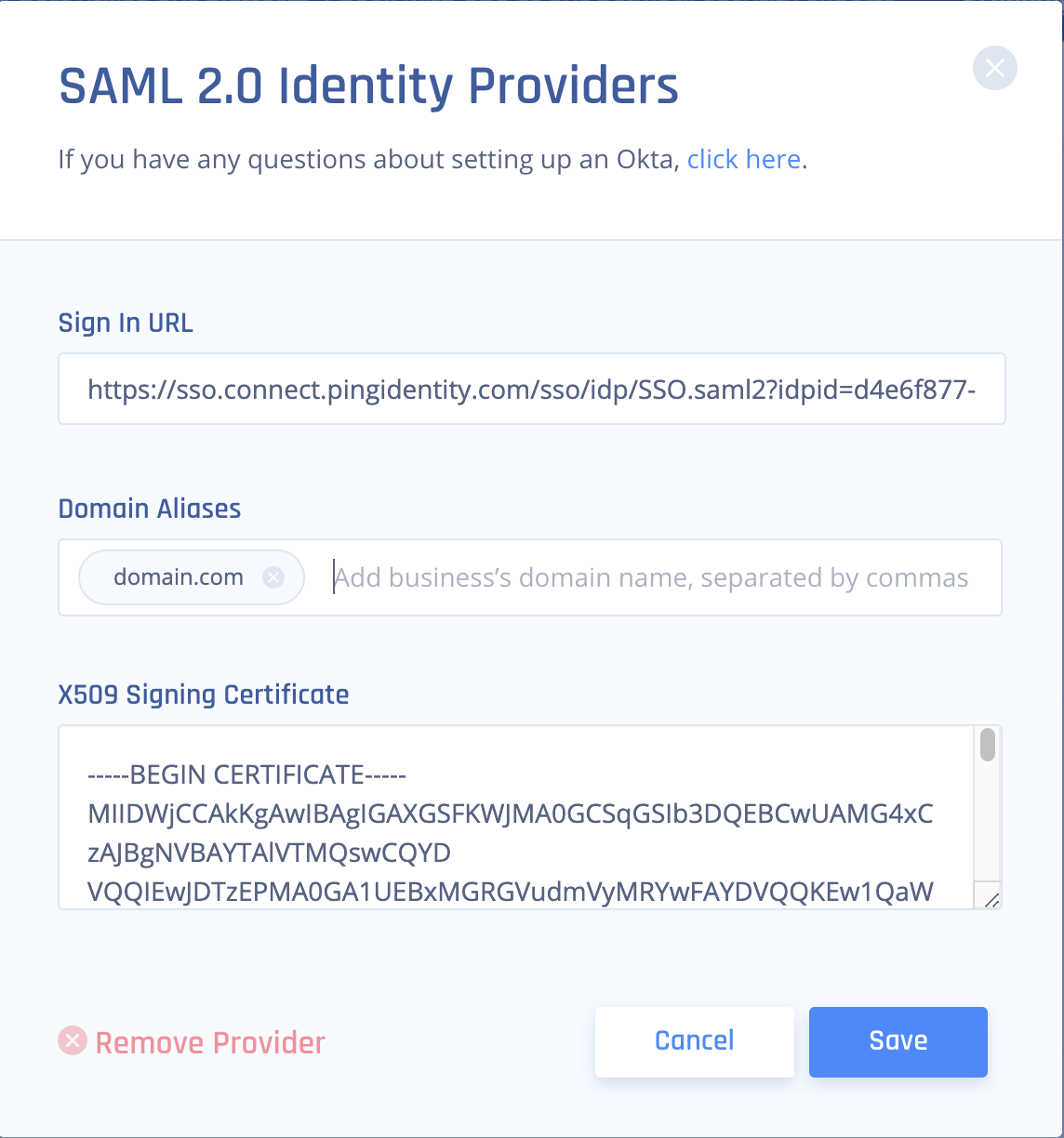
- Select Save.
Recommendations
- When integrating with a SAML IdP, ensure you create a dedicated Harmony SASE Application within your SAML IdP.
- Always replace placeholders like {{WORKSPACE}} with your actual workspace name when setting up.
- Ensure the correct attributes (Email Address, First Name, Last Name) are passed to the platform for accurate member mapping.
- If passing group memberships to Harmony SASE, ensure the correct IdP Object to Harmony SASE Mapping is used
Troubleshooting
If you encounter issues during or after the setup, try reviewing your settings to ensure everything matches the instructions. In particular, check the IP addresses and other details you entered during setup. If issues persist, please consult our dedicated support.
Support Contacts
If you have any difficulties or questions, don't hesitate to contact Harmony SASE's support team. We offer 24/7 chat support on our website at sase.checkpoint.com, or you can email us at sase-support@checkpoint.com. We're here to assist you and ensure your VPN tunnel setup is a success.