Introduction
This guide will help you understand how to establish redundant tunnels between your Harmony SASE network and your Azure Virtual Network Gateway. Redundant tunnels ensure continuous network connectivity even if one of the connections is interrupted.
Breakdown of topics
- Pre-requisites
- Configuration Steps
- Verifying the Setup
- Troubleshooting
- Support Contacts
Pre-requisites
To successfully follow this guide, you should have:
- An active Harmony SASE account and network.
- The Harmony SASE app is installed on your devices.
- An active Azure account with admin permissions.
Create Harmony SASE Gateways
- Your Harmony SASE Network will need to have at least two different gateways in the same network, as listed below.
- Write down the Public IPs for both GWs. Those IPs will be used for the local network gateways on Azure.
- The gateways can be deployed in two separate Regions for comprehensive ISP redundancy.
- The network can be scaled up and adding another region should not affect the connection.
Create a Virtual network gateway on Azure
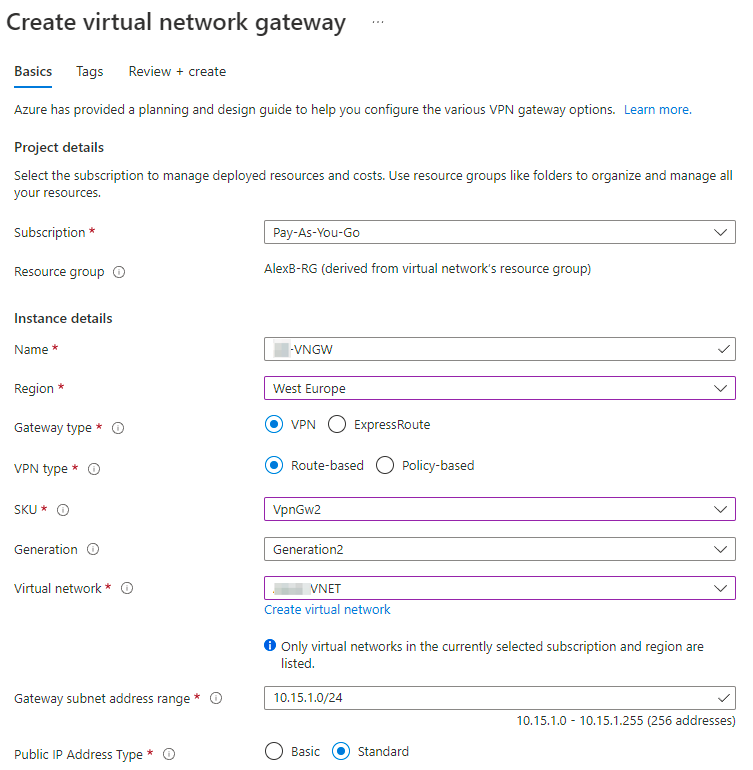
- In your Azure Portal under Virtual network gateways, click on +Create
- Provide the Gateway with a meaningful name.
- Select the relevant Region.
- Gateway type - VPN
- VPN Type - Route-Based
- SKU - Based on your preference and requirements
- Virtual network - Select the relevant VNET
- Gateway subnet address range - (If not filled automatically) Type the address range that was reserved for your Azure gateway (More information can be found in our Single Tunnel guide)
- Public IP address - create new or select existing
- Enable active-active mode - Enabled
- Second Public IP Address - create new or select existing
- Configure GBP - Enabled
- ASN - Leave default or configure based on your preference
- Custom Azure APIPA BGP IP address - leave empty
Create Local network gateways
Next, you will need to create two Local Network Gateways, one for each of your Harmony SASE Gateways:
- In your Azure Portal under Local network gateways, Click on +Create.
- Fill in the following information on the Basic tab.
- Select the relevant resource group.
- Select the relevant Region.
- Provide the Gateway with a meaningful name.
- Endpoint - IP Address.
- IP Address - Type in the Public IP provided in the Harmony SASE web application
- Address Space - Fill in your Permieter81 Address space.
.png)
- Fill in the following information in the Advanced tab:
- Configure BGP settings - Yes
- ASN - can you the default or choose one from the permitted range
- BGP peer IP address - Type any address from the permitted range
- Repeat steps 1-3 for the second Perimtere81 Gateway as well.
Create a connection
- Go to your Local network gateway and click on connections. Press +Add.
- Fill in the following information:
- Name: Enter a meaningful name
- Virtual Private Gateway: Select the Virtual Private Gateway created in the first step of this guide
- Local network gateway: No need to modify (locked)
- Shared key (PSK): Generate a key on the Harmony SASE side, or on a different PSK generating application.
- The key may only contain numbers, letters, and the following characters: “_” and “.”
- Use Azure Private IP Address: leave unchecked
- Enable BGP: Check
- IKE Protocol: IKEv2
- Press OK
- Open the connection you just created and select configuration
- Under IPsec / IKE policy, choose Custom and use the following values to align with the values set in the Harmony SASE's tunnel settings:
Encyrption: AES256
Integrity/PRF: SHA1
DH Group: DHGroup2IPsec Encryption: AES256
IPsec Integrity: SHA1
PFS Group: PFS2IPsec SA lifetime in KiloBytes: 102400000
IPsec SA lifetime in seconds: 27000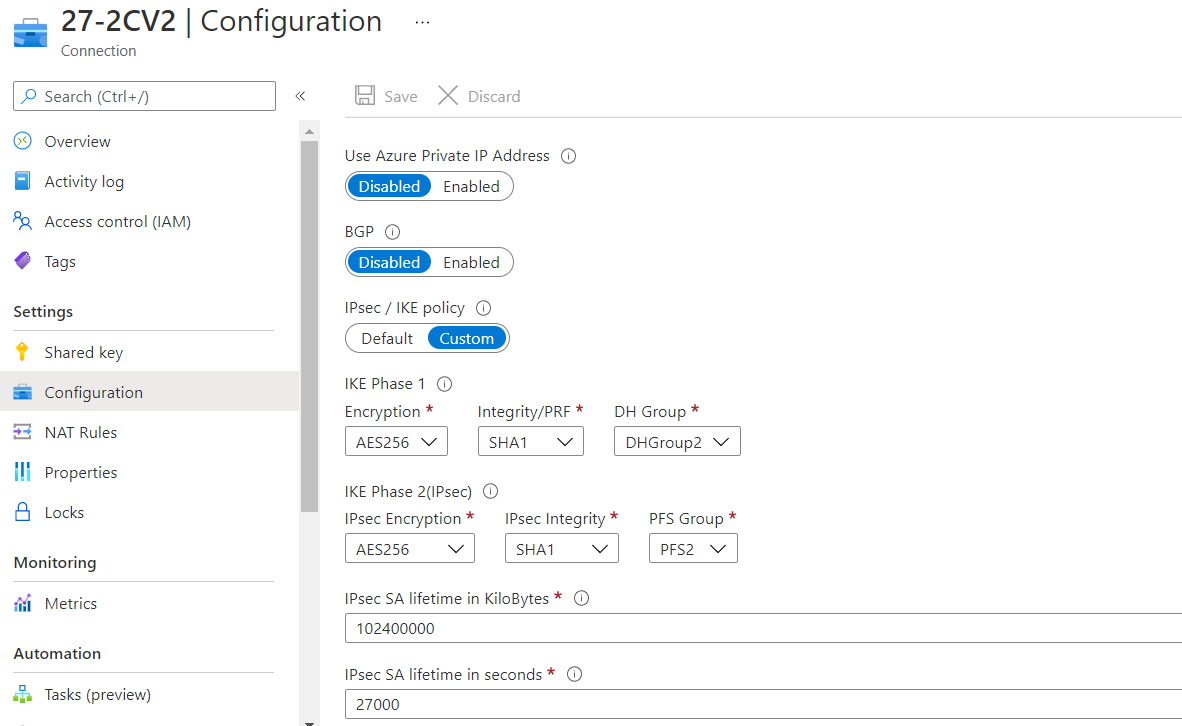
- Create an additional connection for the second Local network gateway
- Download the tunnel configurations (for both Connections):
- Access your Virtual network gateway -> Settings -> Connections -> Click on your 1st connection
- Click on Download configurations
- Device vendor: Generic Samples; Device family: Device Parameters; Firmware version: 1.0
- Download configuration
- Access your Virtual network gateway -> Settings -> Connections -> Click on your 1st connection
Creating the High Availability Harmony SASE Tunnel
- On Your Harmony SASE Admin console, Navigate to your network.
- Click "..." next to one of the gateways and select Add Tunnel.
- Select Redundant Tunnels.
- Select a logical name for your tunnel,
- For example, if your V-Net is located in the EU-West region of Azure, you could name the tunnel "EUWest".
- Copy the values for the first tunnel from untitled file.txt:
- Shared Secret: Pre-Shared Key
Harmony SASE gateway Internal IP: Inside IP Addresses of Customer Gateway - Remote Public IP & Remote ID: Outside IP Addresses of Virtual Private Gateway
Remote Gateway internal IP: Inside IP Addresses of Virtual Private Gateway - Remote Gateway ASN: BGP Configuration Options of Virtual Private Gateway ASN from file
- In Harmony SASE, Tunnel 1 section, specify these:
- Gateway: Harmony SASE Gateway.
- Shared Secret: Character string of your own or click Generate.
- Harmony SASE Gateway Internal IP - Harmony SASE gateway Internal IP for tunnel 1.
- Remote Public IP - Azure tunnel 1 VIP.
- Remote Gateway Internal IP - Azure BGP peer IP1.
- Remote Gateway ASN - Azure BGP ASN.
- Site ID - ID of the remote tunnel is the public IP of the tunnel.
- Shared Secret: Pre-Shared Key
- Repeat step 5 for Tunnel 2, using the values from untitled file(1).txt.
- Under Shared Settings, make sure to select Any(0.0.0.0/0) for both sides. ASN number should remain the same for the Harmony SASE side.
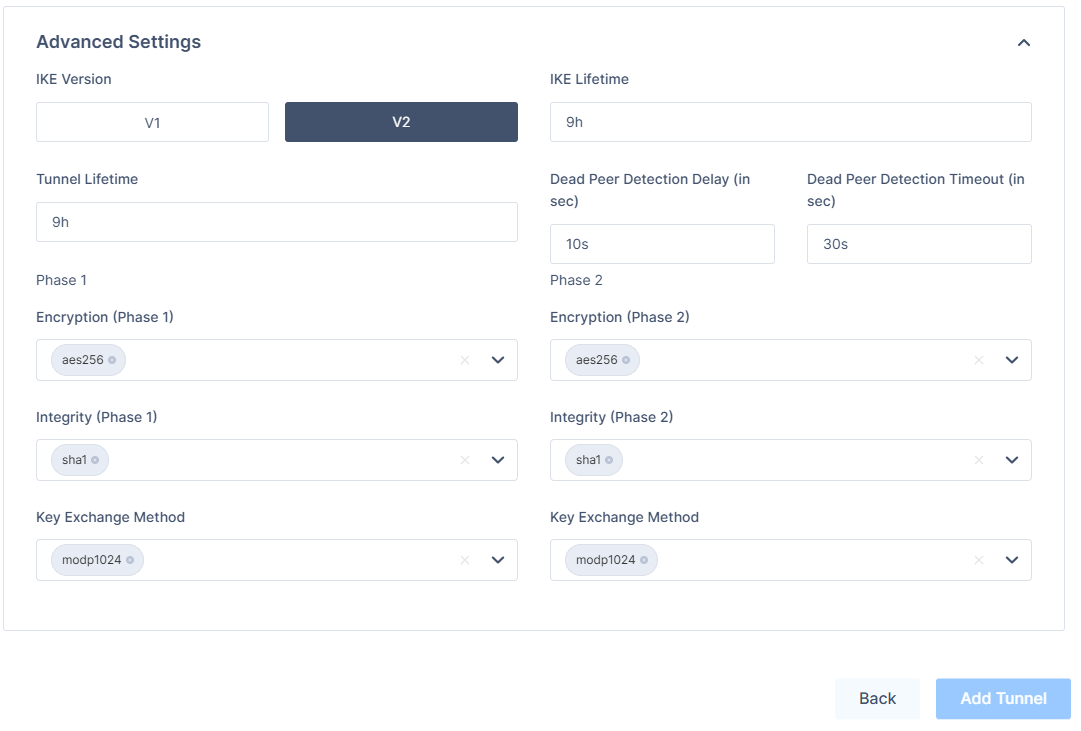
- In the Advanced Settings section, specify these (unless you have configured customer settings on the Azure side):
- IKE Version: V2
- IKE Lifetime: 9h
- Tunnel Lifetime: 9h
- Dead Peer Detection Delay: 10s
- Dead Peer Detection Timeout: 30s
- Phase 1:
- Encryption(Phase 1): aes256
- Integrity (Phase 1): sha1
- Key Exchange Method: modp1024
- Phase 2:
- Encryption(Phase 2): aes256
- Integrity (Phase 2): sha1
- Key Exchange Method: modp1024
- Click Add Tunnel.
Creating Static Routes
- Navigate to your Harmony SASE network and add the route to the corresponding subnet in Azure.
- You'll want to select "..." next to your network and then Routes Table.
- Once that has been completed be sure to select "Apply Configuration" and let the route changes propagate on the Harmony SASE side.
Verifying the Setup
Once set up, your redundant tunnels should be active. To confirm, go to your Harmony SASE dashboard, find the tunnels you started, and ensure their status shows "Up". Connect to your network with the Harmony SASE agent and try accessing resources in your Azure environment.
Troubleshooting
If you encounter issues during or after the setup, try reviewing your settings to ensure everything matches the instructions. In particular, check the IP addresses and other details you entered during setup. If issues persist, please consult our dedicated support.
Support Contacts
If you have any difficulties or questions, don't hesitate to contact Harmony SASE's support team. We offer 24/7 chat support on our website at sase.checkpoint.com, or you can email us at sase-support@checkpoint.com. We're here to assist you and ensure your VPN tunnel setup is a success.
.PNG)
.PNG)