Introduction
This guide will walk you through the steps to set up redundant VPN tunnels between your Harmony SASE network and your AWS Virtual Private Gateway environment. This ensures higher availability for your network connections.
Note: This setup specifically aids in achieving redundancy by utilizing two independent gateways.
Breakdown of topics:
1. Pre-requisites
2. Configuration Steps
3. Verifying the Setup
4. Troubleshooting
5. Support Contacts
Pre-requisites
To successfully follow this guide, you should have:
An active Harmony SASE account and network.
The Harmony SASE app is installed on your devices.
An active AWS account with the necessary permissions.
Configuration Steps
Create Harmony SASE Gateways
- Your Harmony SASE Network will need to have at least two different gateways in the same network, as listed below.
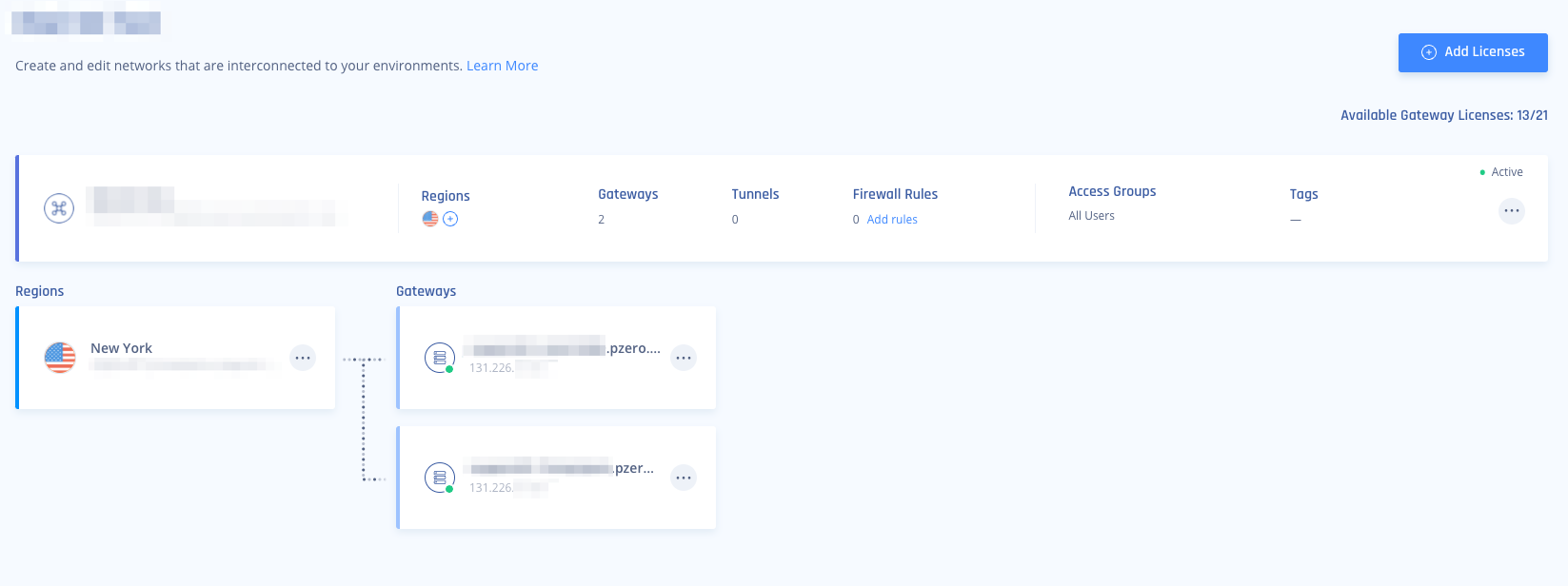
- These gateways can be deployed in two separate Regions for comprehensive ISP redundancy
- The network can be scaled up, and adding another region should not affect the connection
Create a Virtual Private Gateway
- You can skip this step if you already have a Virtual Private Gateway in your AWS region already
- On the left pane, under Virtual Private Network (VPN) click on Virtual Private Gateways and then Create a Virtual Private Gateway.
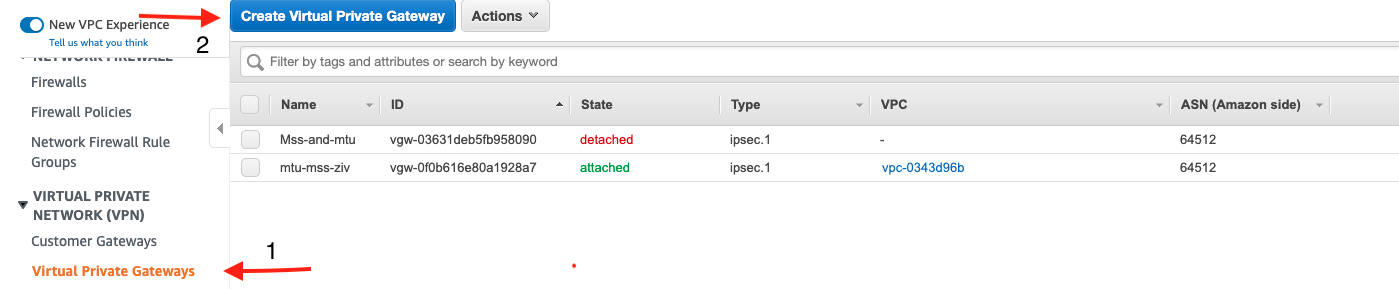
- Create a Virtual Private Gateway with Default Settings
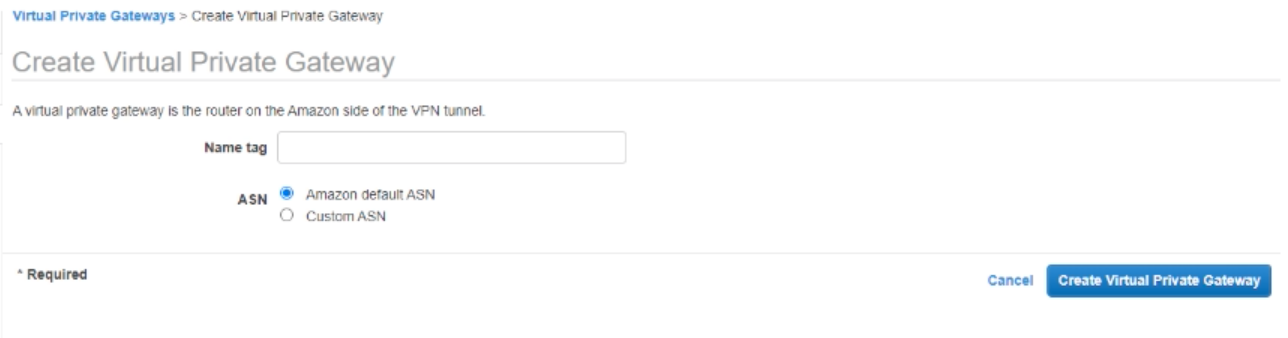
- Select the newly created Virtual Private Gateway, on top click on "Actions" and "Attach to VPC"
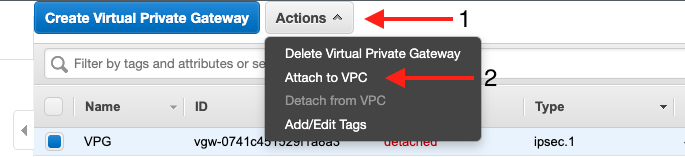
- A pop-up will appear, select the relevant VPC from the list
- On the left pane, under Virtual Private Network (VPN) click on Customer Gateway and then Create Customer Gateway.
- Routing is Dynamic, under IP Address, enter the first Harmony SASE Gateway IP
You can keep the BGP AS Number for the Harmony SASE gateway at 64512.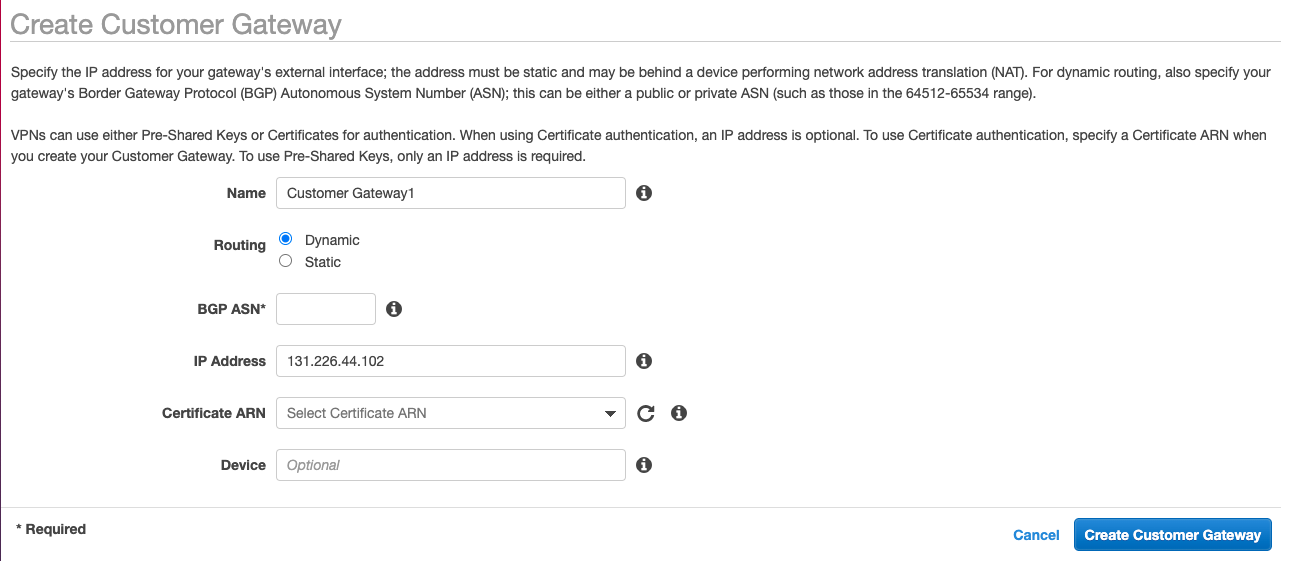
- Repeat the above steps, this time, under IP address use the Second Harmony SASE Gateway IP
Create two Site-to-Site VPN connections
- In your AWS VPC under VIRTUAL PRIVATE NETWORK(VPN) Click Site-to-Site VPN Connections, then Create VPN Connection.
- Under Target Gateway Type select Virtual Private Gateway, for Virtual Private Gateway select the first Virtual Private Gateway created.
For Customer Gateway, select Existing, and under Customer Gateway ID pick the first Customer Gateway created.
Routing is Dynamic (BGP).
The rest of the options should remain unchanged.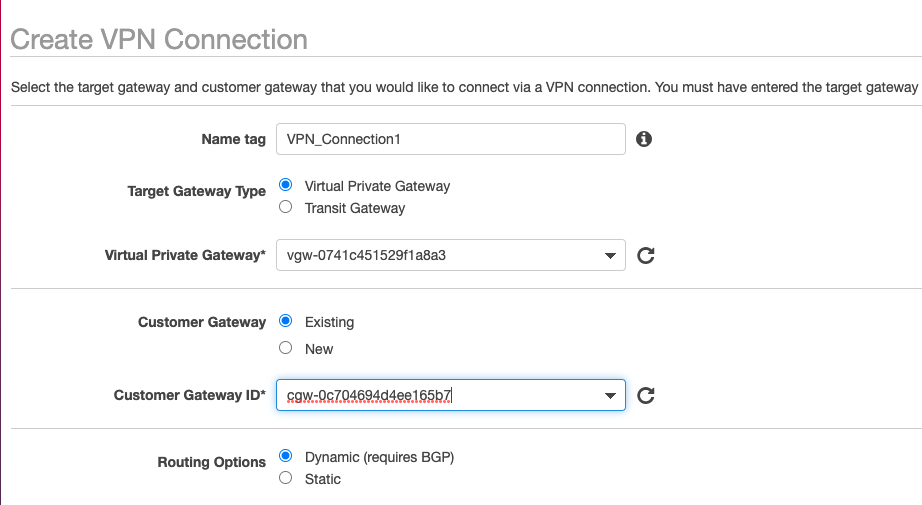
- Click Download Configuration.
- Be sure to choose Generic under Vendor, and Ikev2 for Ike Version.
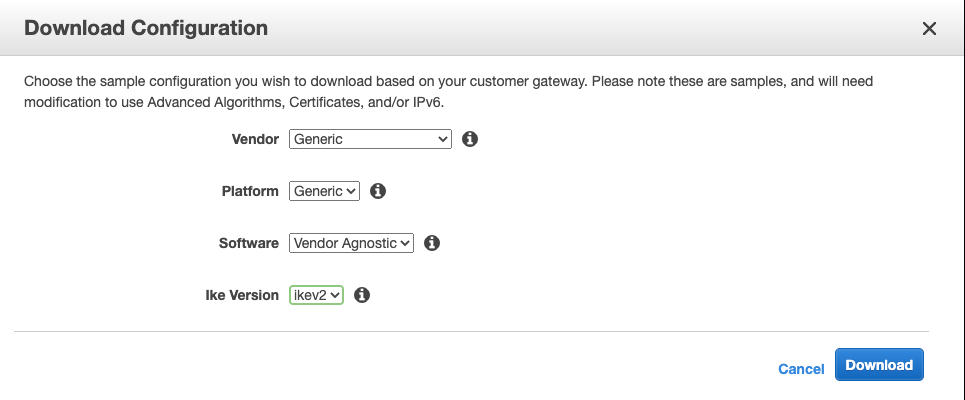
- Download and rename the file Tunnel1.txt
- Repeat steps 1-5, this time, select the other Customer Gateway.
- Rename the second file you downloaded Tunnel2.txt
Creating the High Availability Harmony SASE Tunnel
- In Your Harmony SASE Admin console, Navigate to your network.
- Click "..." next to one of the gateways and select Add Tunnel.
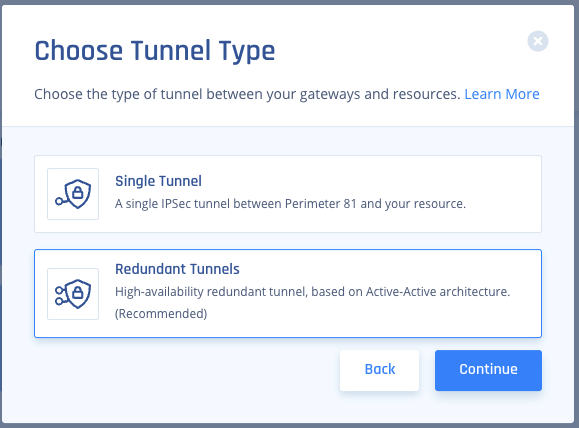
- Choose IPSEC Site-2-Site Tunnel, then Continue.
.png)
- Select Redundant Tunnels, and afterward click Continue.
- Select a logical name for your tunnel,
- For example, if your Transit gateway is located in the US-East region of AWS, you could name the tunnel "USEast". If this is your Staging environment, call it "Staging".
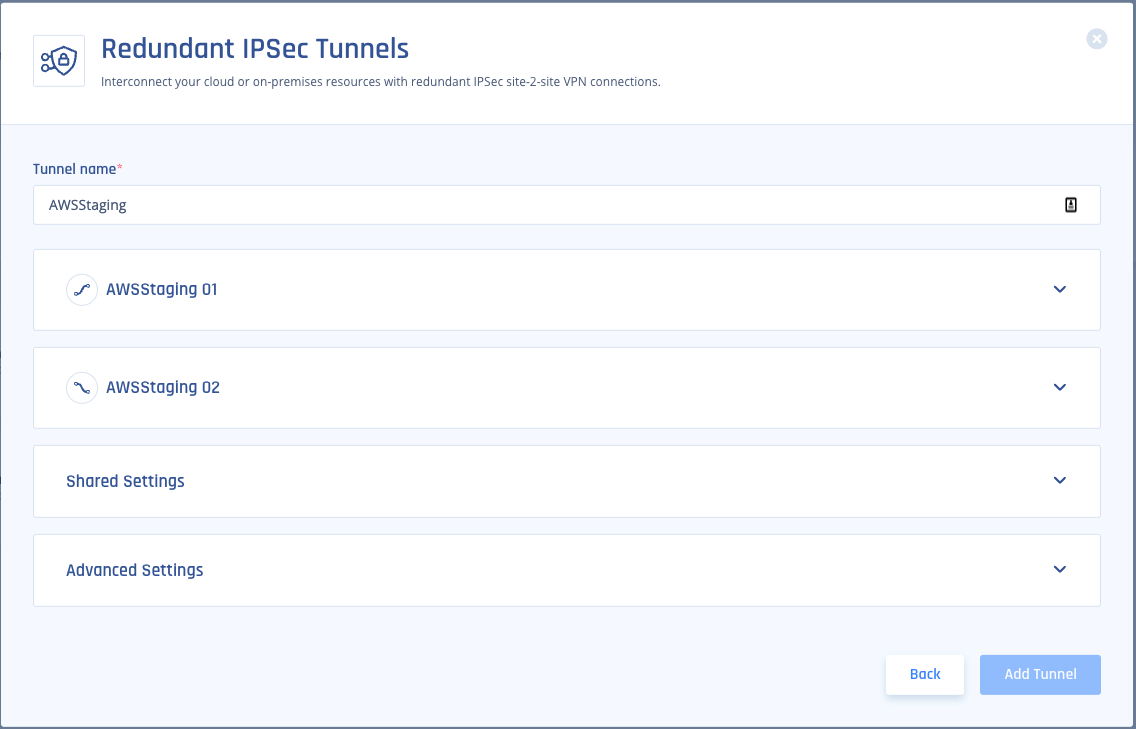
- For example, if your Transit gateway is located in the US-East region of AWS, you could name the tunnel "USEast". If this is your Staging environment, call it "Staging".
- Copy the values for the first tunnel from Tunnel1.txt:
- Shared Secret: Pre-Shared Key
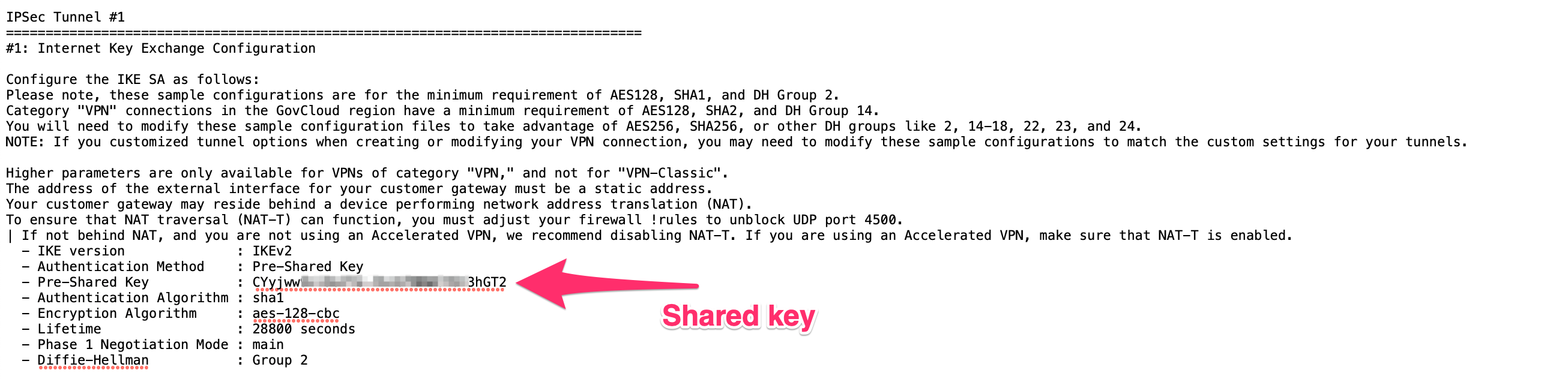
- Harmony SASE gateway Internal IP: Inside IP Addresses of Customer Gateway.
- Remote Public IP & Remote ID: Outside IP Addresses of Virtual Private Gateway.
- Remote Gateway internal IP: Inside IP Addresses of Virtual Private Gateway. The IP on AWS side has a subnet (/30) that should be discarded when pasting.
- Remote Gateway ASN: BGP Configuration Options of Virtual Private Gateway ASN from file.
.png)
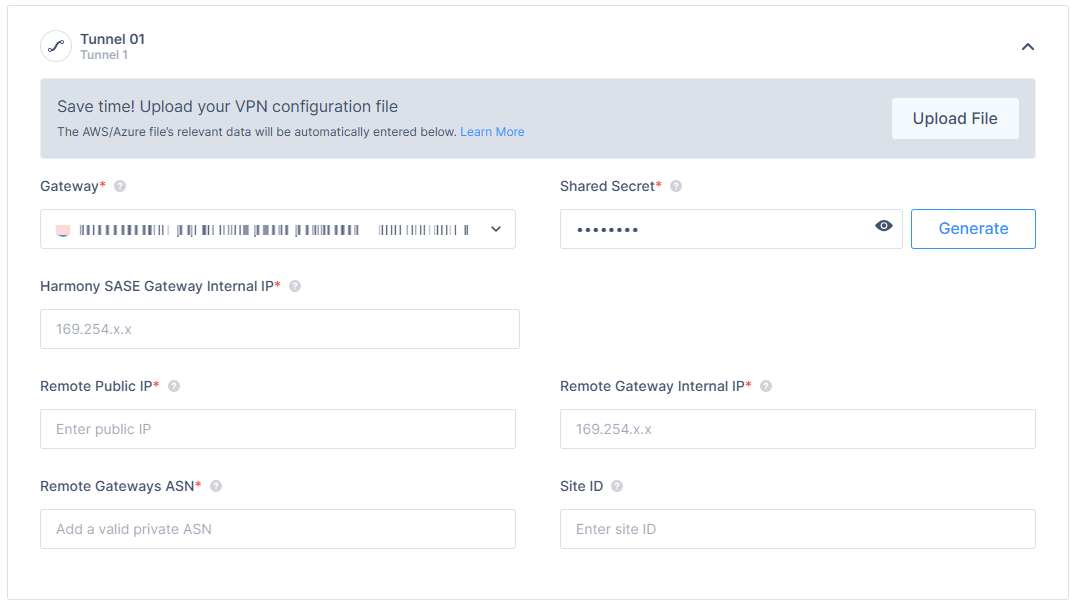
- In the Tunnel 1 section, specify these:
- Gateway: Harmony SASE Gateway.
- Shared Secret: Enter a character string of your own or use Generate.
- Harmony SASE Gateway Internal IP - Harmony SASE Internal IP for tunnel 1.
- Remote Public IP - AWS Gateway external IP.
- Remote Gateway Internal IP - AWS Gateway internal IP.
- Remote Gateway ASN - AWS ASN.
- Site ID - ID of the remote tunnel is the public IP of the tunnel.
- Shared Secret: Pre-Shared Key
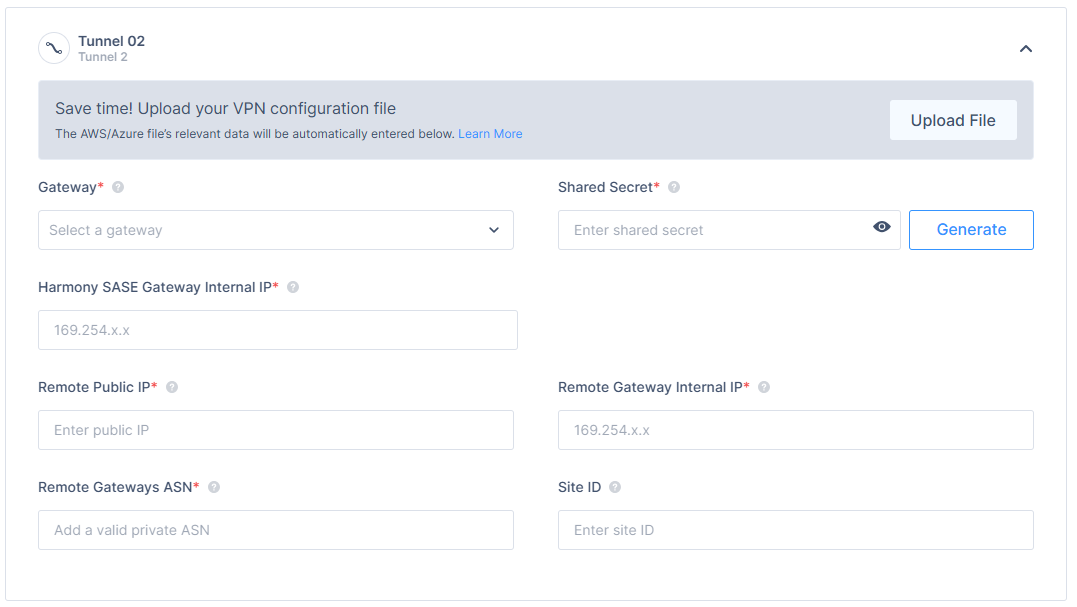
- In the Tunnel 2 section, specify these:
- Gateway: Harmony SASE Gateway.
- Shared Secret: Enter a character string of your own or use Generate.
- Harmony SASE Gateway Internal IP - Harmony SASE Internal IP for tunnel 1.
- Remote Public IP - AWS Gateway external IP.
- Remote Gateway Internal IP - AWS Gateway internal IP.
- Remote Gateways ASN - AWS ASN.
- Site ID - ID of the remote tunnel is the public IP of the tunnel.
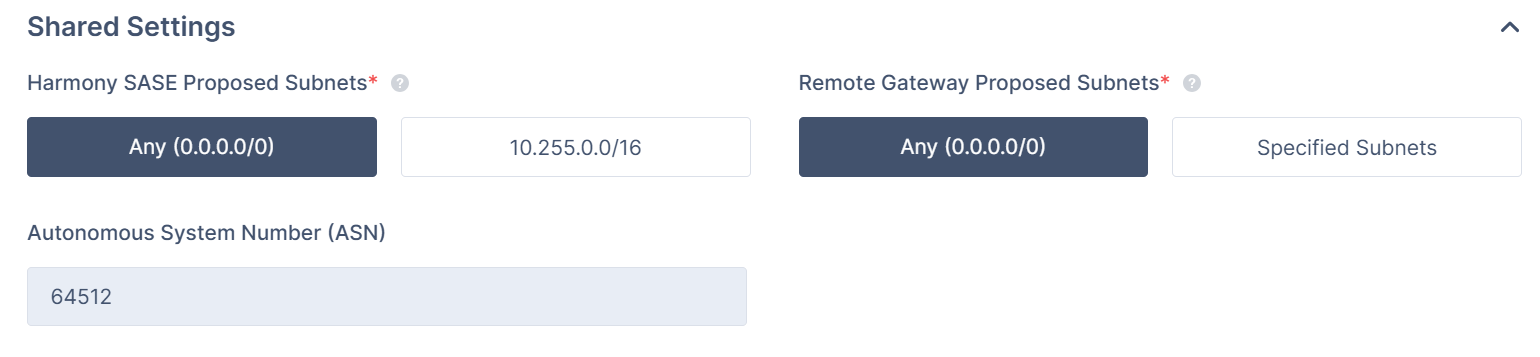
- In the Shared Secrets section, specify these:
- Harmony SASE Proposal Subnets: Leave Any (0.0.0.0/0) selected.
- Remote Gateway Proposal Subnets: Leave Any (0.0.0.0/0) selected.
- ASN - 64512
- In the Advanced Settings section, specify these:
- IKE Version: V2
- IKE Lifetime: 8h
- Tunnel Lifetime: 1h
- Dead Peer Detection Delay: 10s
- Dead Peer Detection Timeout: 30s
- Phase 1:
- Encryption(Phase 1): aes256
- Integrity (Phase 1): sha512
- Key Exchange Method: ecp521
- Phase 2:
- Encryption(Phase 2): aes256
- Integrity (Phase 2): sha512
- Key Exchange Method: ecp521
- Click Add Tunnel.
Creating Static Routes
- Navigate to VPC -> Select the corresponding VPC that is attached to the Virtual Private Gateway-> Select the Main Route Table for the VPC.
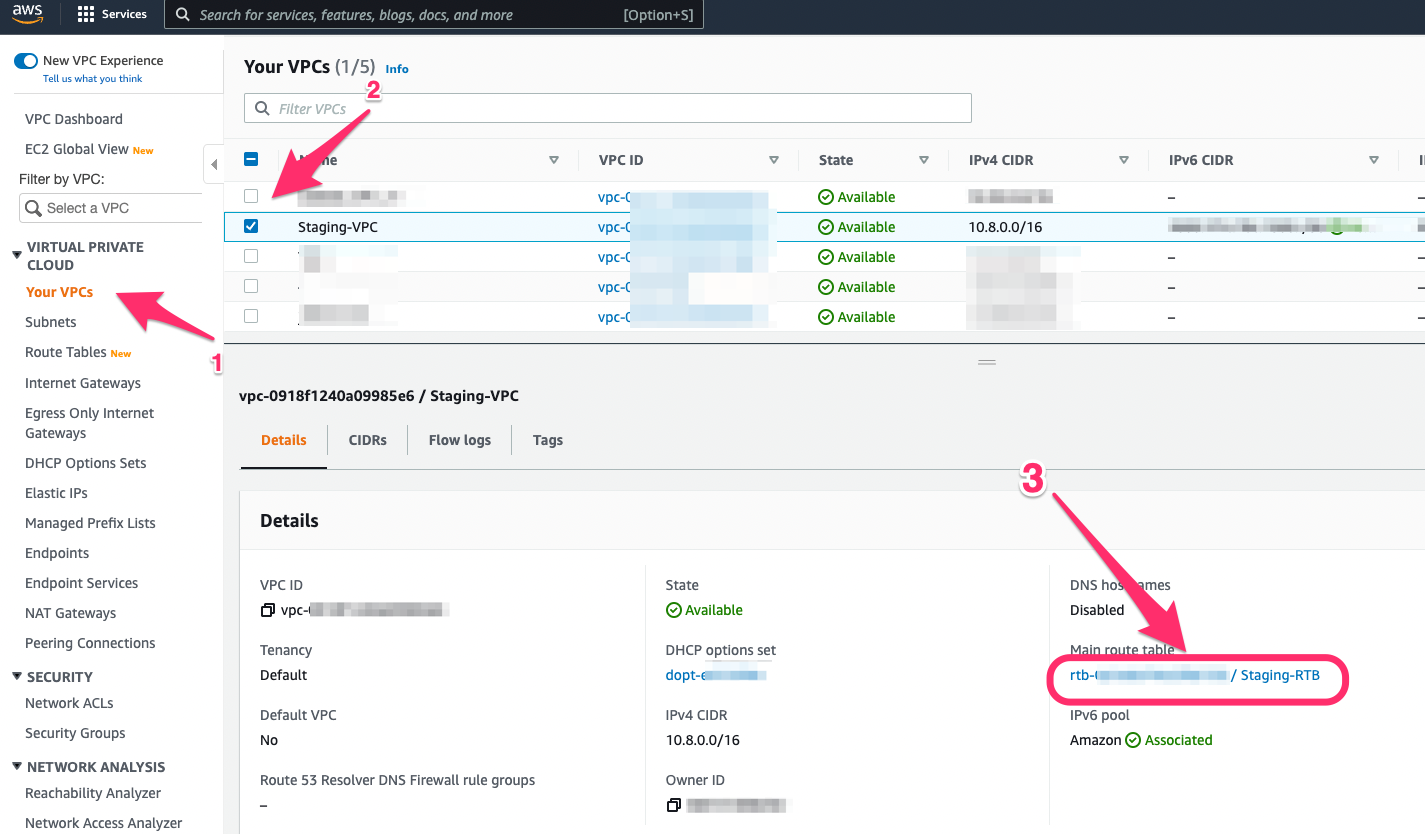
- Edit the main Route Table for the VPC and add the subnet mask of your Harmony SASE network as the destination with the Virtual Private Gateway as the target (Route for reverse traffic).
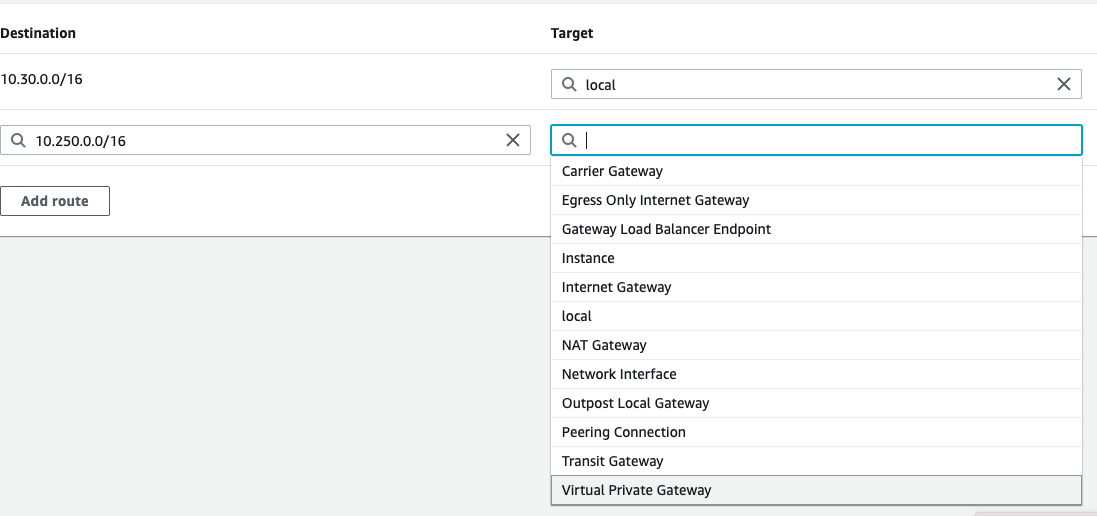
- Please note that this might not the Main Route Table for the VPC; In that case, you will need to locate each subnet that's associated with the VPC and add the reverse route for the Perimeter81 internal subnet range.
- Navigate back to your Harmony SASE network and add the route to the corresponding subnet in AWS.
You'll want to select "..." next to your network and then Routes Table.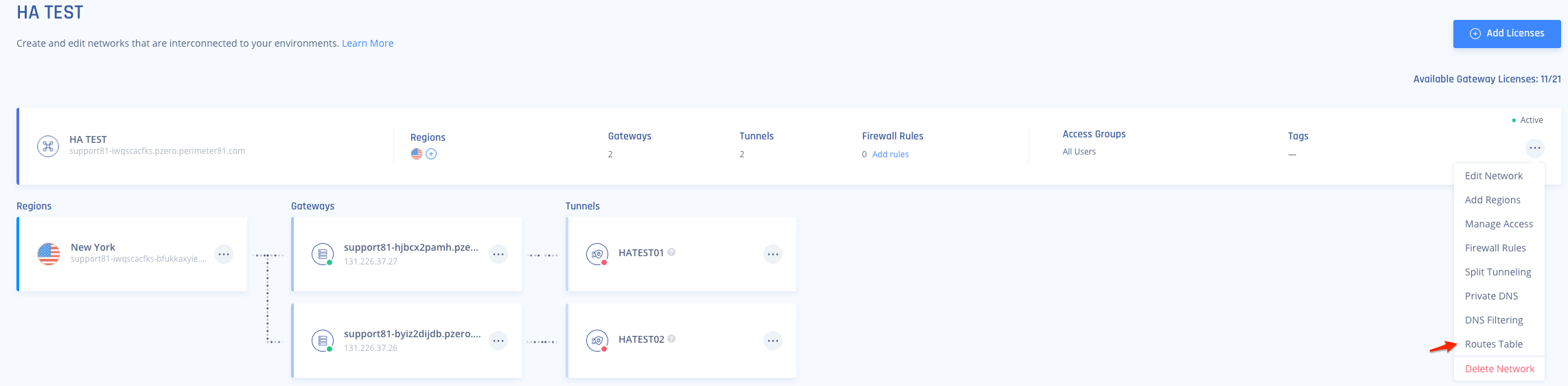
- Once that has been completed, be sure to select "Apply Configuration" and let the route changes propagate on the Harmony SASE network.
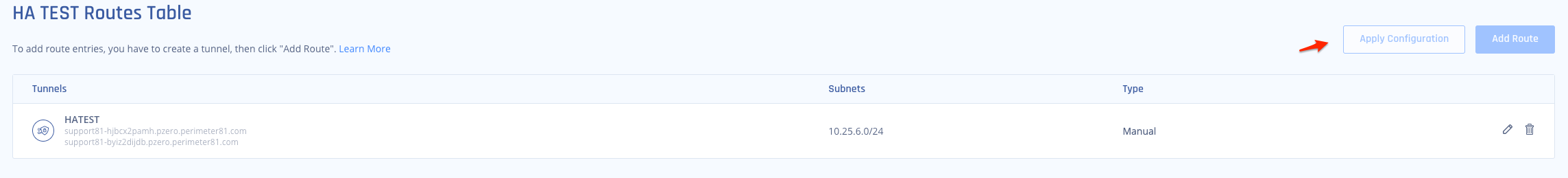 Route SharedPlease ensure that the route added matches the route transmitted by BGP. Any discrepancies, such as incorrect subnetting or supernetting, are strictly prohibited.
Route SharedPlease ensure that the route added matches the route transmitted by BGP. Any discrepancies, such as incorrect subnetting or supernetting, are strictly prohibited.
Verifying the Setup
Once set up, your redundant tunnels should be active. To confirm, go to your Harmony SASE dashboard, find the tunnels you started, and ensure their status shows "Up". Connect to your network with the Harmony SASE agent and try accessing resources in your AWS environment.
Troubleshooting
If you encounter issues during or after the setup, try reviewing your settings to ensure everything matches the instructions. In particular, check the IP addresses and other details you entered during setup. If issues persist, please consult our dedicated support.
Support Contacts
If you have any difficulties or questions, don't hesitate to contact Harmony SASE's support team. We offer 24/7 chat support on our website at sase.checkpoint.com, or you can email us at sase-support@checkpoint.com. We're here to assist you and ensure your VPN tunnel setup is a success.
.png)
.PNG)