Introduction
Welcome to our guide on setting up a Site-to-Site VPN tunnel between your Harmony SASE network and the Cisco ASA (Route-based) environment.
Breakdown of topics
- Pre-requisites
- Configuration Steps
- Verifying the Setup
- Troubleshooting
- Support Contacts
Pre-requisites
To successfully follow this guide, ensure that:
- An active Harmony SASE account and a configured network.
- The Harmony SASE application is installed on your devices.
- An active Cisco ASA (Route-based) setup with necessary administrative permissions.
Configuration Steps
Configuring an IPSec Tunnel in the Management Platform
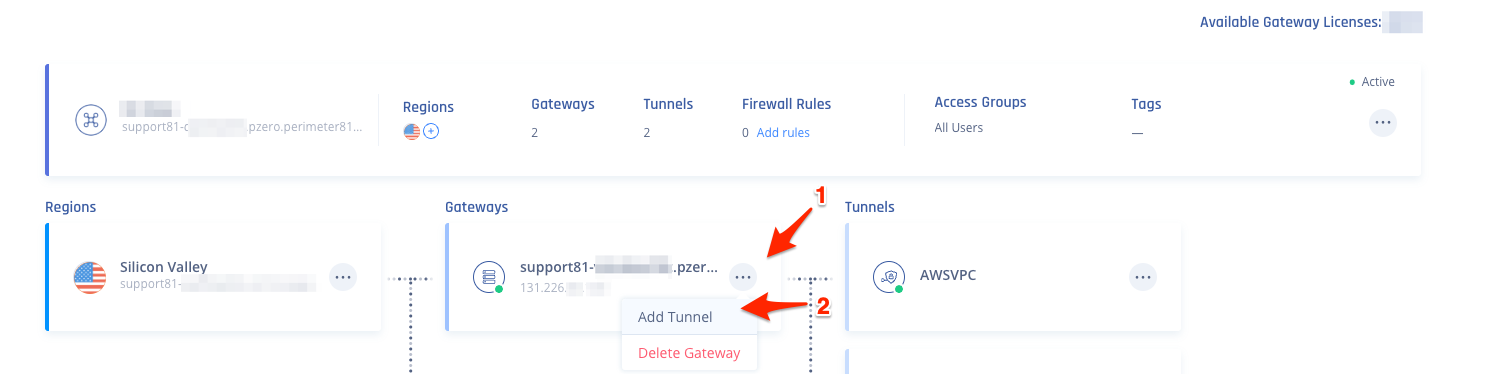
- In the Harmony SASE Management Console, open the Networks menu, and navigate to the network from which you want to create the tunnel to the Cisco ASA Firewall.
- Select the three-dotted menu (...) and select Add Tunnel.
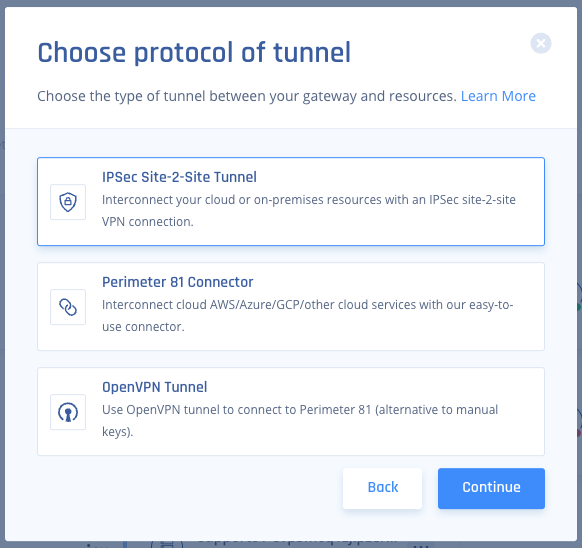
- Select IPSec Site-2-Site Tunnel and select Continue.
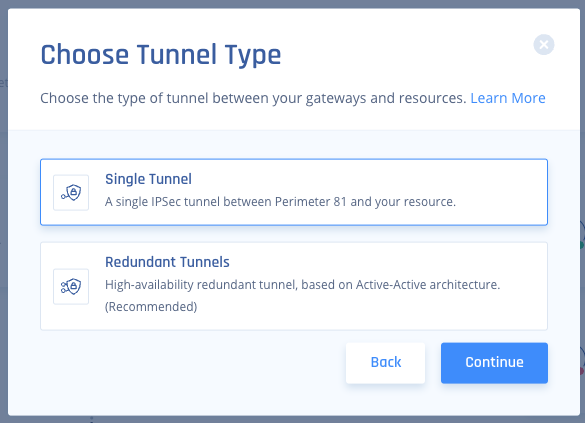
- Select Single Tunnel, and Click Continue.
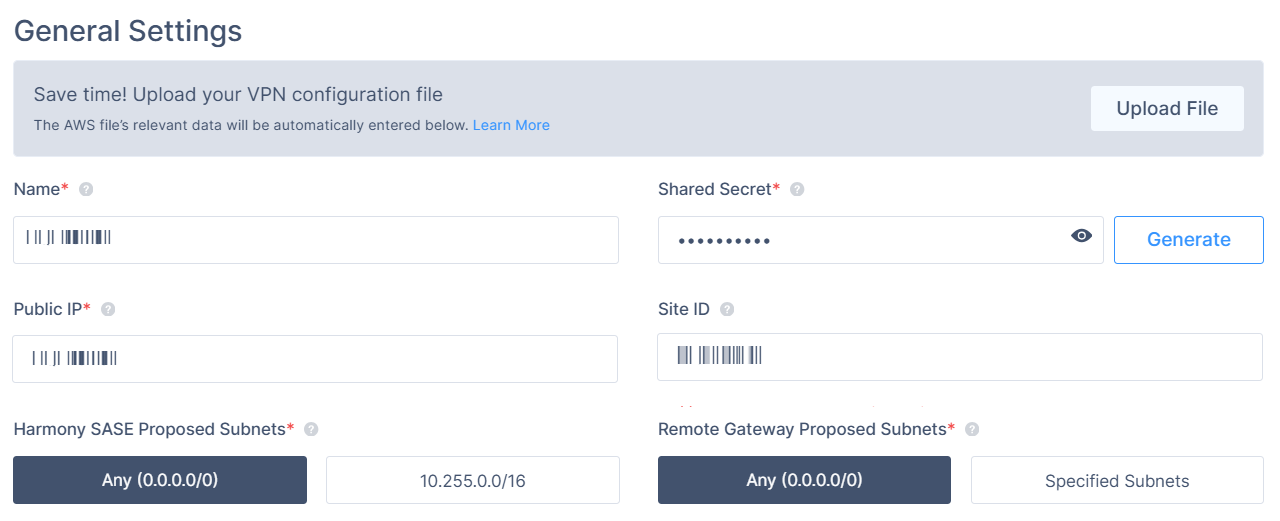
- In the General Settings section, specify these:
- Name: Choose whatever name you find suitable for the tunnel.
- Shared Secret: Insert a string of your own or use Generate.
- Public IP: Insert the public IP of the ASA device.
- Remote ID: Insert the remote ID of the ASA device (this will be the same as Public IP unless the device is behind a NAT, then use the IP of the "outside" interface on the ASA.)
- Harmony SASE Gateway Proposal Subnets: Leave Any (0.0.0.0/0) selected here.
- Remote Gateway Proposal Subnets: Leave Any (0.0.0.0/0) selected here.
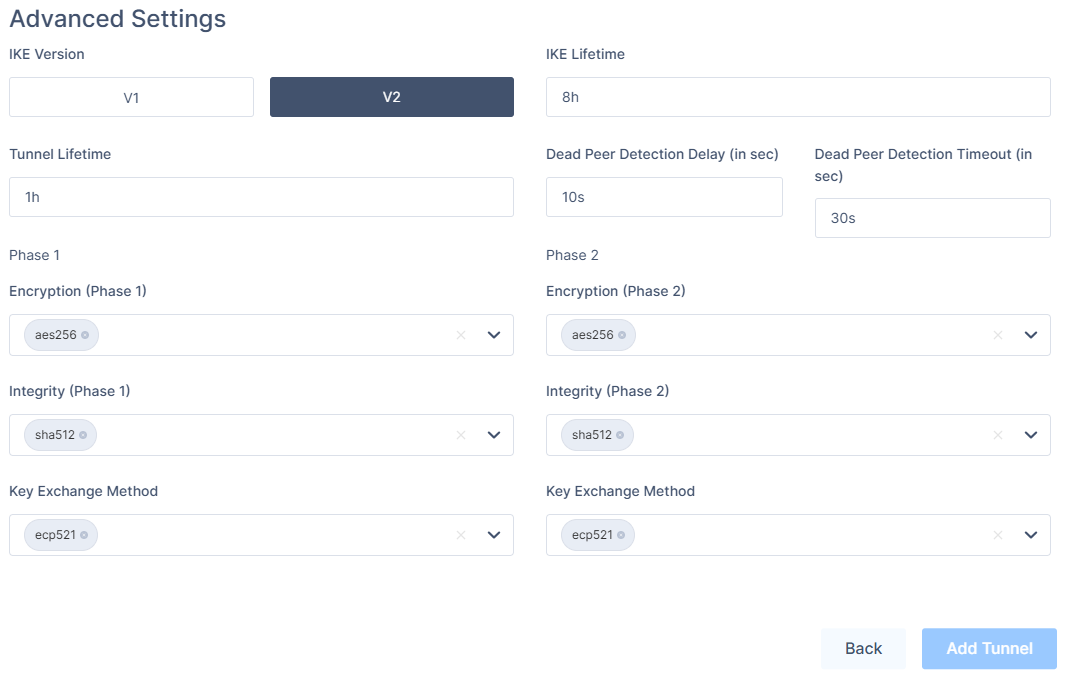
- In the Advanced Settings section, specify these:
- IKE Version: IKEv2
- IKE Lifetime: 8h
- Tunnel Lifetime: 1h
- Dead Peer Detection Delay: 10s
- Dead Peer Detection Timeout: 30s
- Phase 1
- Encryption (Phase 1): aes256
- Integrity (Phase 1): sha512
- Key Exchange Method: ecp521
- Phase 2
- Encryption (Phase 2): aes256
- Integrity (Phase 2): sha512
- Key Exchange Method: ecp521
- Click Add Tunnel.
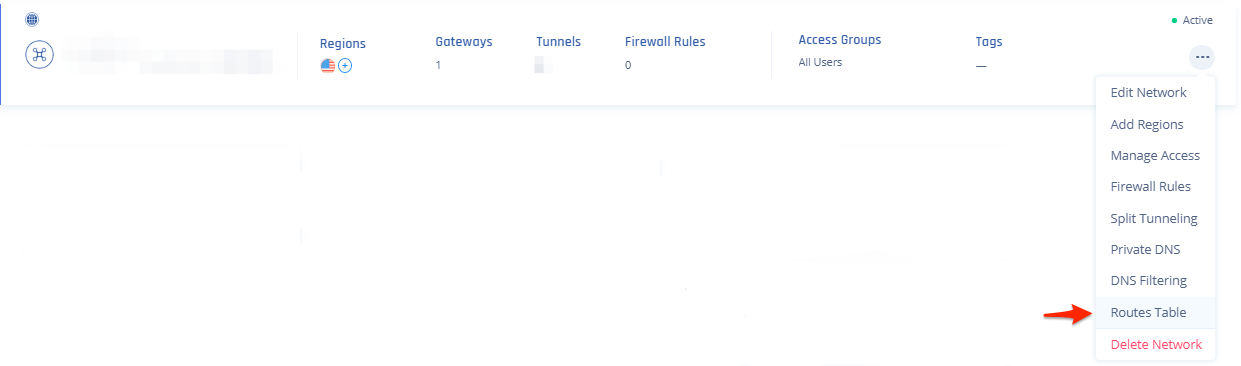
- On your network select your three dots and click on Routes Table:
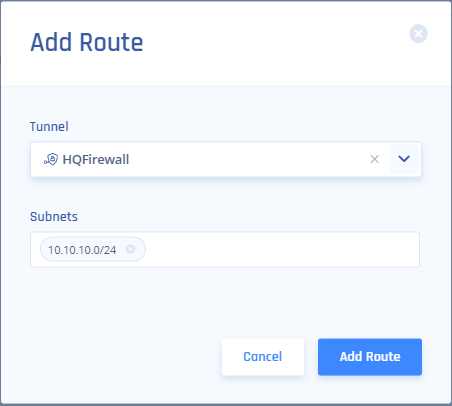
- Click the Add Route button on the top right, then on this popup fill out accordingly (Tunnel will match the name above, and Subnets will be the subnets you want to reach on the other side of the tunnel) and click the Add Route button:
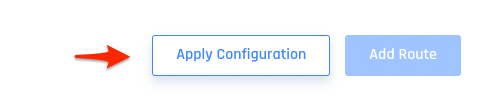
- Be sure to click Apply Configuration when done.
Configuring the tunnel in the ASA (CLI)
Do either CLI or ASDM (below), not both!
In this next part, please adjust the following values according to your unique site configurations:
- outside - Your public-facing interface in the Cisco ASA.
- 131.226.X.X - Your Harmony SASE gateway IP.
- SuperSecret - Your Shared Secret for the tunnel.
- 10.255.0.0/16 - Your Harmony SASE network subnet range. (10.255.0.0/16 by default)
This document also makes the following assumptions about your device:
- You have never configured IKEv2 policies on this device. (policy 10)
- You have never enabled IKEv2 on the outside interface. (crypto ikev2 enable outside)
Steps:
- SSH into your ASA with a privilege-15-level account and then enter enable mode.
- Start by creating a tunnel profile and proposal(these will need to match the settings you configured on Harmony SASE):
crypto ipsec ikev2 ipsec-proposal Tun-Prop protocol esp encryption aes-256 protocol esp integrity sha-512 crypto ipsec profile Tun-Prof set ikev2 ipsec-proposal Tun-Prop set pfs group21 set security-association lifetime seconds 3600 - Next, create a crypto policy (these will need to match the settings you configured on Harmony SASE):
crypto ikev2 policy 10 encryption aes-256 integrity sha512 group 21 prf sha512 lifetime seconds 28800 crypto ikev2 enable outside - Select IPsec IKEv2 Tunnels and create a new tunnel, then fill in the following information:
group-policy Tun-Grp-Pol internal group-policy Tun-Grp-Pol attributes vpn-tunnel-protocol ikev2 tunnel-group 131.226.X.X type ipsec-l2l tunnel-group 131.226.X.X general-attributes default-group-policy Tun-Grp-Pol tunnel-group 131.226.X.X ipsec-attributes ikev2 remote-authentication pre-shared-key SuperSecret ikev2 local-authentication pre-shared-key SuperSecret - Create your Virtual Tunnel Interface (VTI). Please be sure to use the IP address in the text:
interface Tunnel1 nameif P81_131.226.X.X ip address 169.254.2.122 255.255.255.252 tunnel source interface outside tunnel destination 131.226.X.X tunnel mode ipsec ipv4 tunnel protection ipsec profile Tun-Prof - Create a route back to the Harmony SASE subnet:
route P81_131.226.X.X 10.255.0.0 255.255.0.0 169.254.2.121 1
Configuring the tunnel in the ASA (ASDM)
Do either CLI (above) or ASDM, not both!
Like the CLI configurations, please adjust the following values according to your unique site configurations:
- outside - Your public-facing interface in the Cisco ASA.
- 131.226.X.X - Your Harmony SASE gateway IP.
- SuperSecret - Your Shared Secret for the tunnel.
- 10.255.0.0/16 - Your Harmony SASE network subnet range. (10.255.0.0/16 by default)
This document also makes the following assumptions about your device:
- You have never configured IKEv2 policies on this device. (policy 10)
- You have never enabled IKEv2 on the outside interface. (crypto ikev2 enable outside)
Steps:
- Login to your device using ASDM.
- Start by creating a tunnel profile and proposal (these will need to match the settings you configured on Harmony SASE).
- Click on Configuration > Site-to-site VPN > Advanced > IPsec Proposals (Transform Sets):
- Add an IKEv2 IPsec Proposal by clicking the Add button under the IKE v2 IPsec Proposals section:
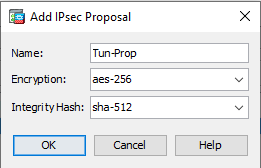
Name: Tun-Prop Encryption:aes-256 Integrity Hash: sha-512 - Add an IPsec Profile by clicking the Add under the IPsec Profile section:
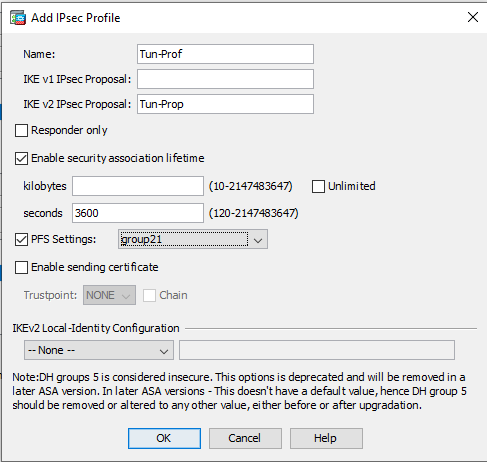
Name: Tun-Prop IKE v2 IPsec Proposal: Tun-Prof (use the same name as above under the IKEv2 IPsec Proposal, in our example Tun-Prop) Enable Security association lifetime: kilobytes (leave blank) seconds: 3600 PFS Settings: group21
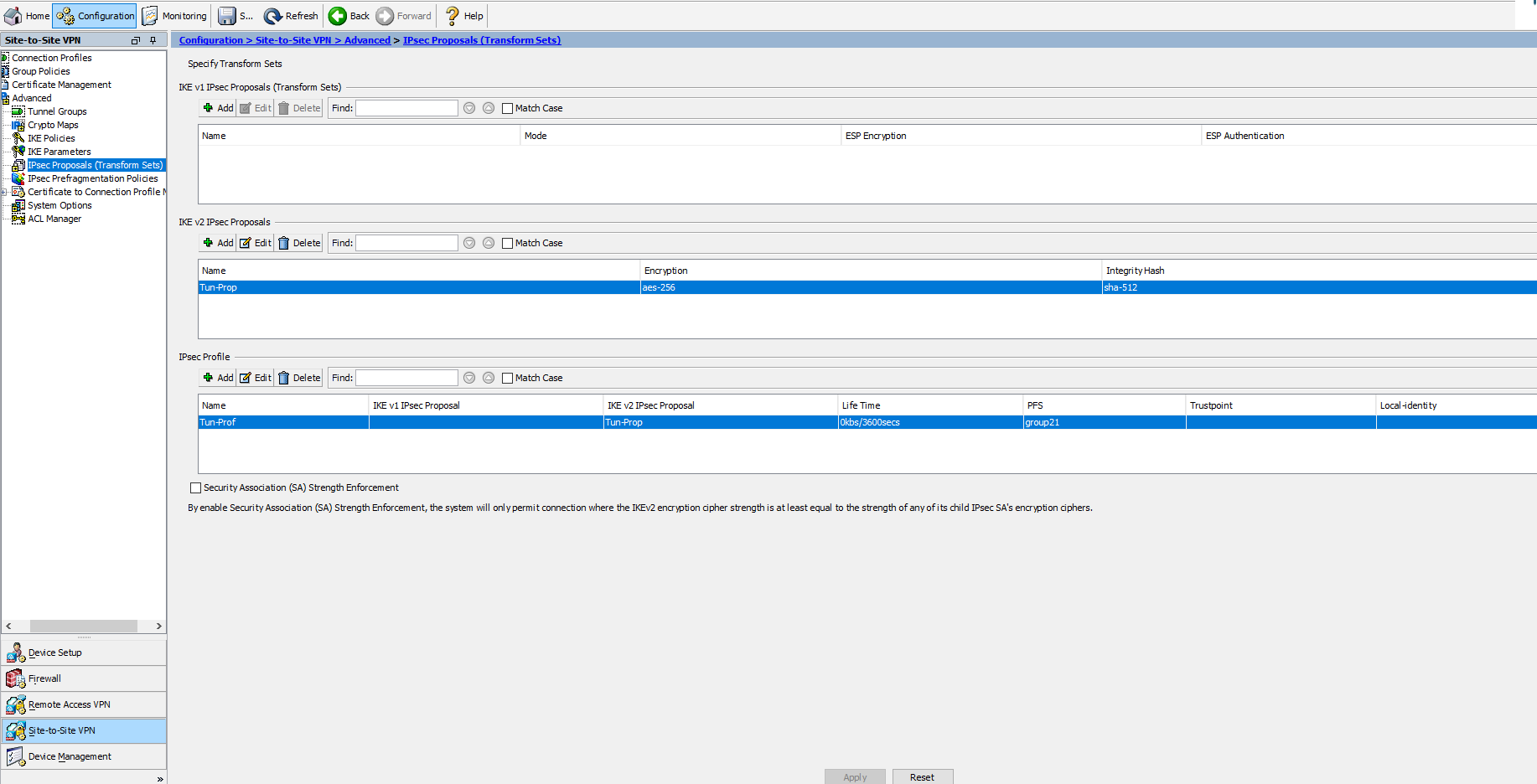
- Click on Configuration > Site-to-site VPN > Advanced > IPsec Proposals (Transform Sets):
- After that is done you should have a screen like this, click Apply and Save.
- Next, make a crypto policy by navigating to Configuration > Site-to-Site VPN > Advanced > IKE Policies. These will need to match the settings you configured on Harmony SASE.
- Add an IKE v2 Policy Proposal by clicking the Add button under the IKEv2 Policies:
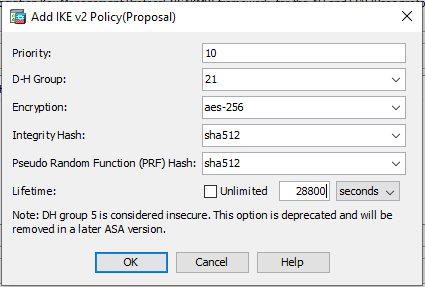
Priority: 10 D-H Group: 21 Encryption: AES-256 Integrity Hash: sha512 Pseudo-Random Function (PRF) Hash: sha512 Lifetime: 28800 seconds
- Add an IKE v2 Policy Proposal by clicking the Add button under the IKEv2 Policies:
- Navigate to Configuration > Site-to-Site VPN > Group Policies and click the Add button
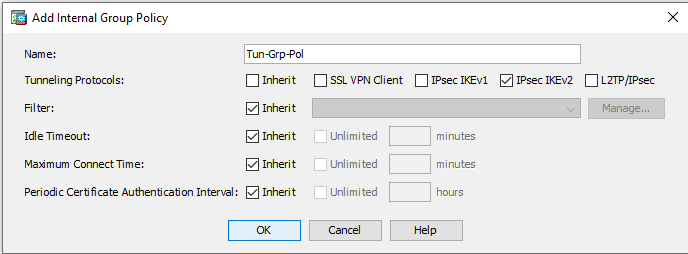
Name: Tun-Grp-Pol (this can be any name you want, but will be used in the next step) Tunneling Protocols: only select IPsec IKEv2 - Navigate to Configuration > Site-to-Site VPN > Advanced > Tunnel Groups and click the Add button:
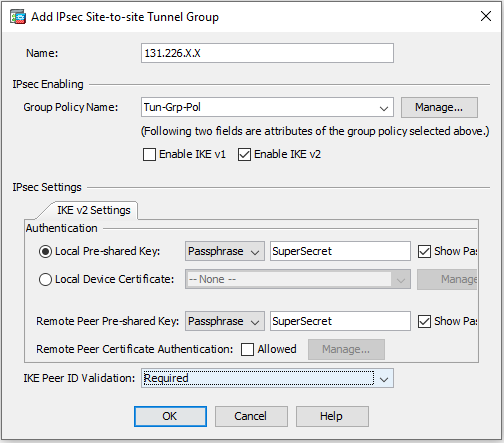
Text Name: 131.226.X.X (This should match the Harmony SASE Gateway IP) Group Policy Name: Tun-Grp-Pol (from the last step) Local Pre-Shared Key: SuperSecret (Same key as on Harmony SASE) Remote Pre-Shared Key: SuperSecret (Same key as on Harmony SASE) - Navigate to Configuration > Device Setup > Interface Settings > Interfaces and click the down by the Add button then select VTI Interface:
- On the General tab:
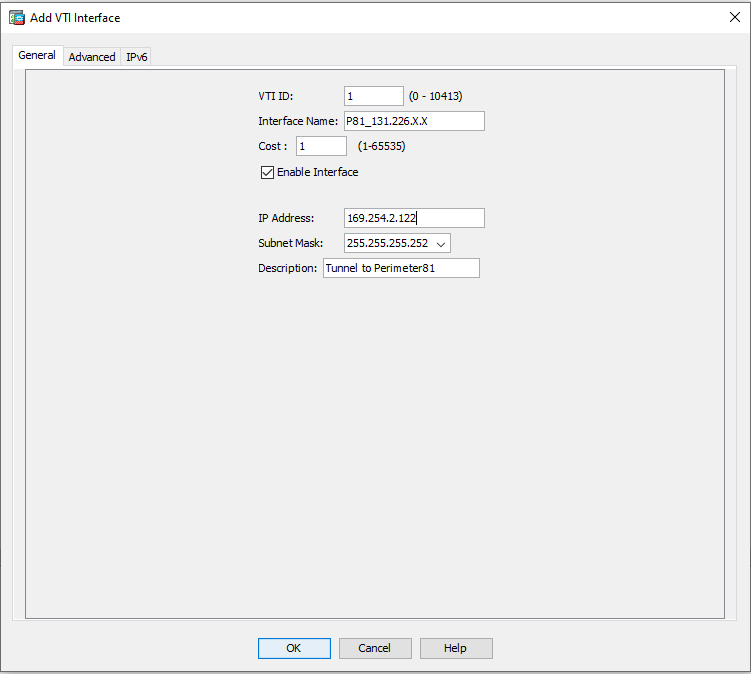 Text
TextVTI ID: 1 Interface Name: P81_131.226.X.X IP Address: 169.254.2.122 255.255.255.252 (use this IP) Subnet Mask: 255.255.255.252 (use this mask) Description: Tunnel to Perimeter81 (Optional) - Click on the Advanced tab:
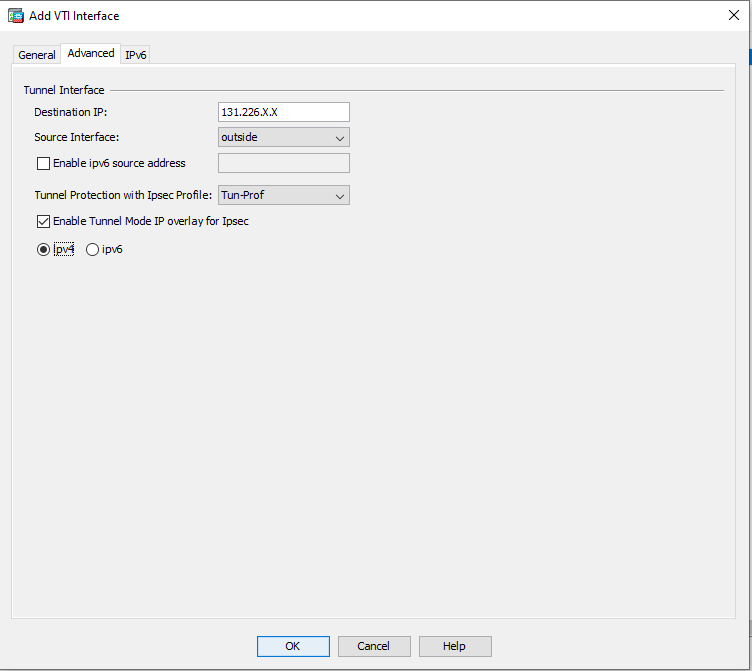 Text
TextDestination IP: 131.226.X.X (Harmony SASE Gateway IP Source Interface: outside (name of your outside interface) Tunnel Protection with Ipsec Profile: Tun-Prof Put a checkmark next to Enable Tunnel Mode IP overlay for Ipsec and select the Ipv4 radio button
- On the General tab:
- Create a route back to the Harmony SASE subnet:
- Start by creating a Network Object for the Harmony SASE network by navigating to Configuration > Firewall > Objects > Network Objects/Groups then clicking the Add > Network Object button:
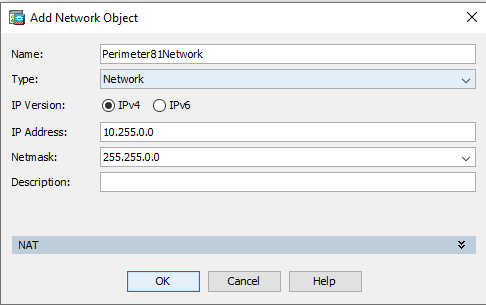
Name: Perimeter81Network Type: Network IP Version: IPv4 IP Address: 10.255.0.0 (make this the same as your Harmony SASE Network range) Netmask: 255.255.0.0 (or a /16 in CIDR notation, this should match with your Harmony SASE network as well) - Next create a gateway object by navigating to Configuration > Firewall > Objects > Network Objects/Groups then clicking the Add > Network Object button:
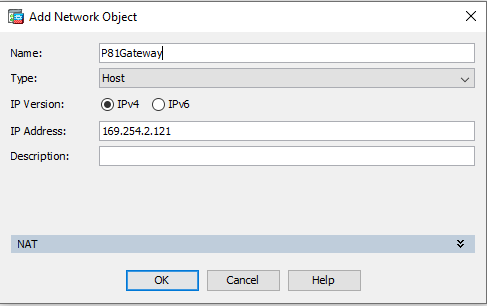
After these are created hit the Apply button.Name: P81Gateway Type: Host IP Version: IPv4 IP Address: 169.254.2.121 (use this address) - Finally navigate to Configuration > Device Setup > Routing > Static Routes then click the Add button:
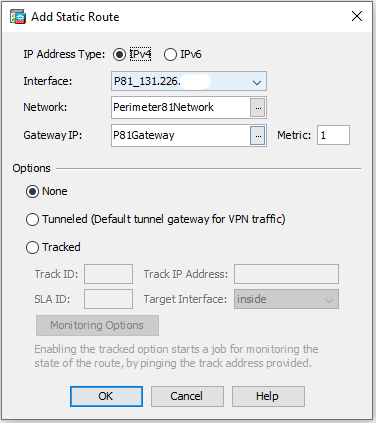
IP Address Type: IPv4 Interface: P81_131.226.X.X (Same name as tunnel interface above) Network: Perimeter81Network (Use the 3 dots to select) Gateway IP: P81Gateway (Use the 3 dots to select)
- Start by creating a Network Object for the Harmony SASE network by navigating to Configuration > Firewall > Objects > Network Objects/Groups then clicking the Add > Network Object button:
Verifying the Setup
After following the above steps, your tunnel should be active.
To verify, go to your Harmony SASE dashboard, locate the tunnel you just created, and check the tunnel status.
It should indicate that the tunnel is "Up", signifying a successful connection.
Next, connect to your network using the Harmony SASE agent and attempt to access one of the resources in your environment.
Troubleshooting
If you encounter issues during or after the setup, try reviewing your settings to ensure everything matches the instructions. In particular, check the IP addresses and other details you entered during setup. If issues persist, please consult our dedicated support.
Support Contacts
If you have any difficulties or questions, don't hesitate to contact Harmony SASE's support team. We offer 24/7 chat support on our website at sase.checkpoint.com, or you can email us at sase-support@checkpoint.com. We're here to assist you and ensure your VPN tunnel setup is a success.