Understanding Zero Trust Policies and Rules
Zero Trust Application Access Policies enable you to define granular level permissions to ensure that only authorized users have access to specific applications.
Policies and rules are an additional layer of security for our Zero Trust Applications.
They provide Administrators and Managers with the ability to set granular sets of rules into Policies that will limit access to internal and cloud resources based on Groups, Date and Time, Geo-location, Operating Systems, Browsers, and much more.
How to Set Up Zero Trust Policies and Rules
Creating an Application Access Policy
- Access the Harmony SASE Administrator Portal and click Private Access > Application Policies.
- Click Add Policy.
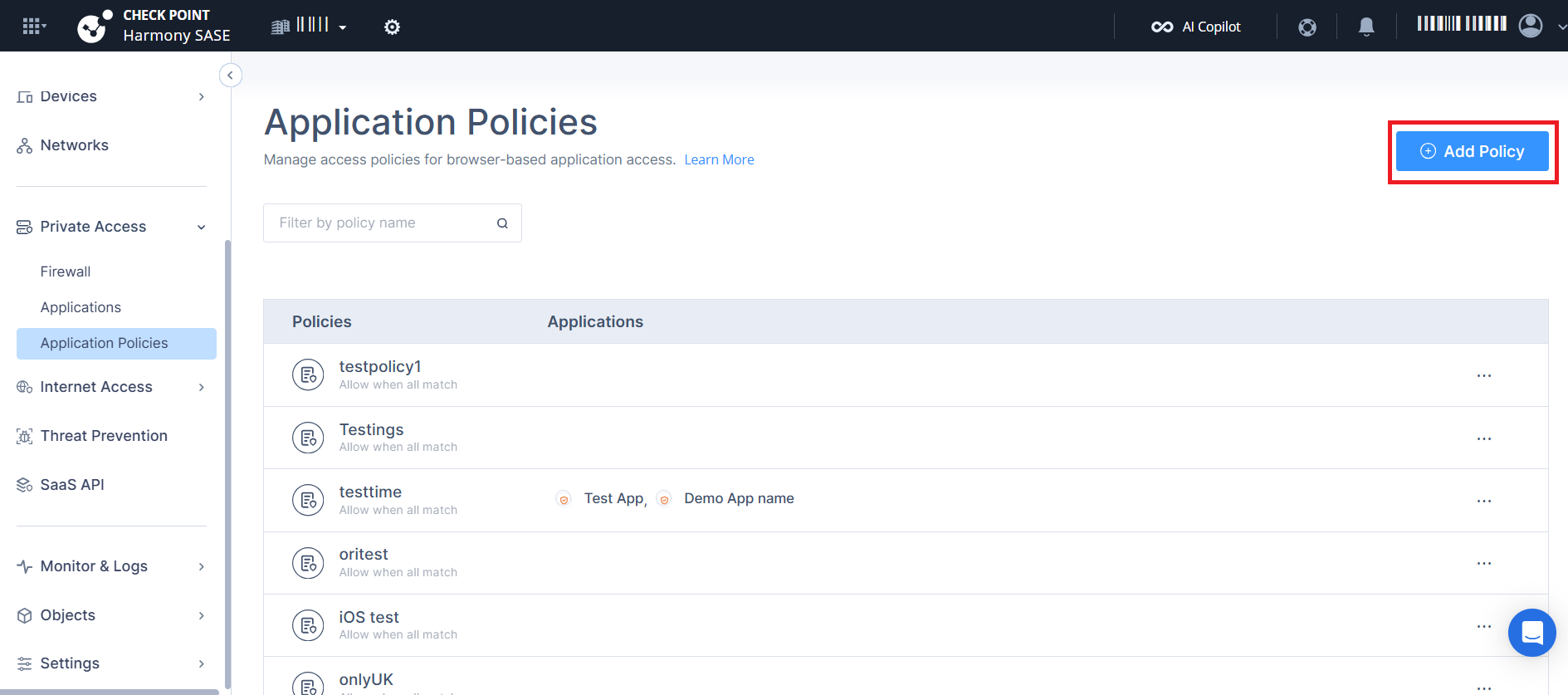 The Add New Policy page appears.
The Add New Policy page appears.
- Enter these:
- Policy Name - Name of the policy.
- Logical Operator
- From the policy action list, select either of these:
- Allow
- Deny
- From the list, select one of these:
- When All Match – The policy is considered compliant only if all defined rules are met.
- When Some Match– The policy is considered compliant if at least one defined rule is met.
- Example 1: When all match
Assume you have configured an application policy with the Allow action and the When all match condition: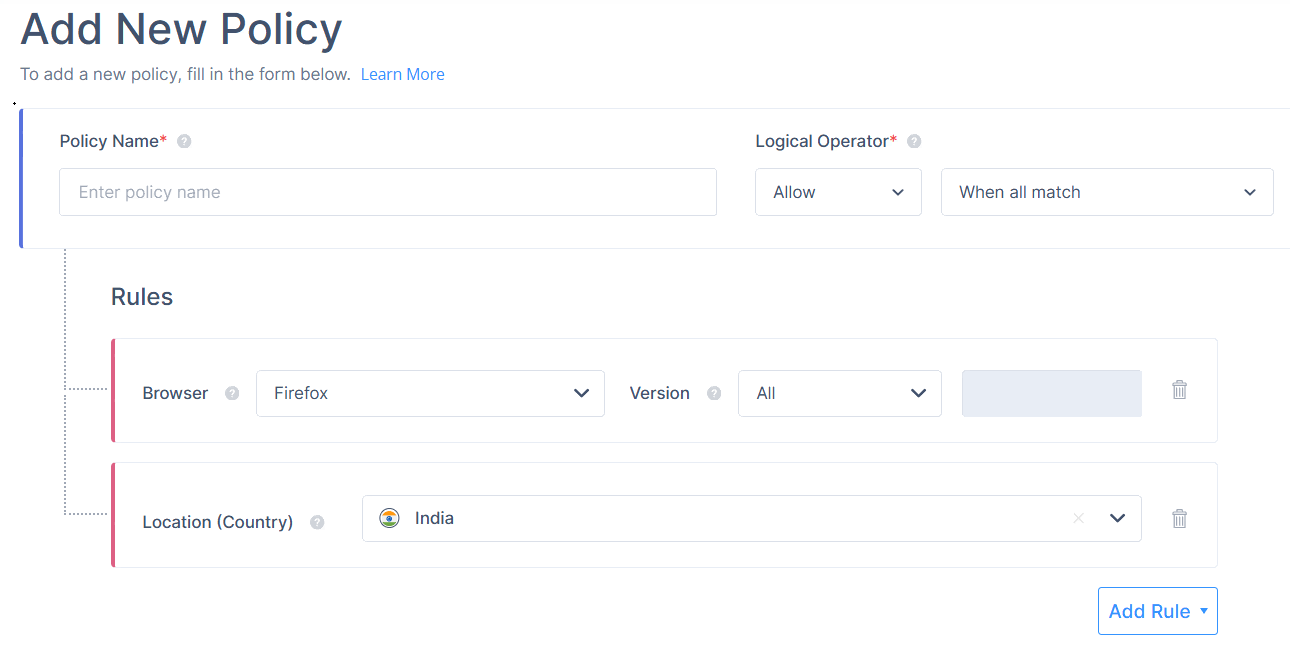
- Browser: Firefox
- Location (Country): India
In this case, access is allowed only if the user is using the Firefox browser and is located in India.
- Example 2: When some match
Now, assume the same application policy is configured with the Allow action and the When some match condition: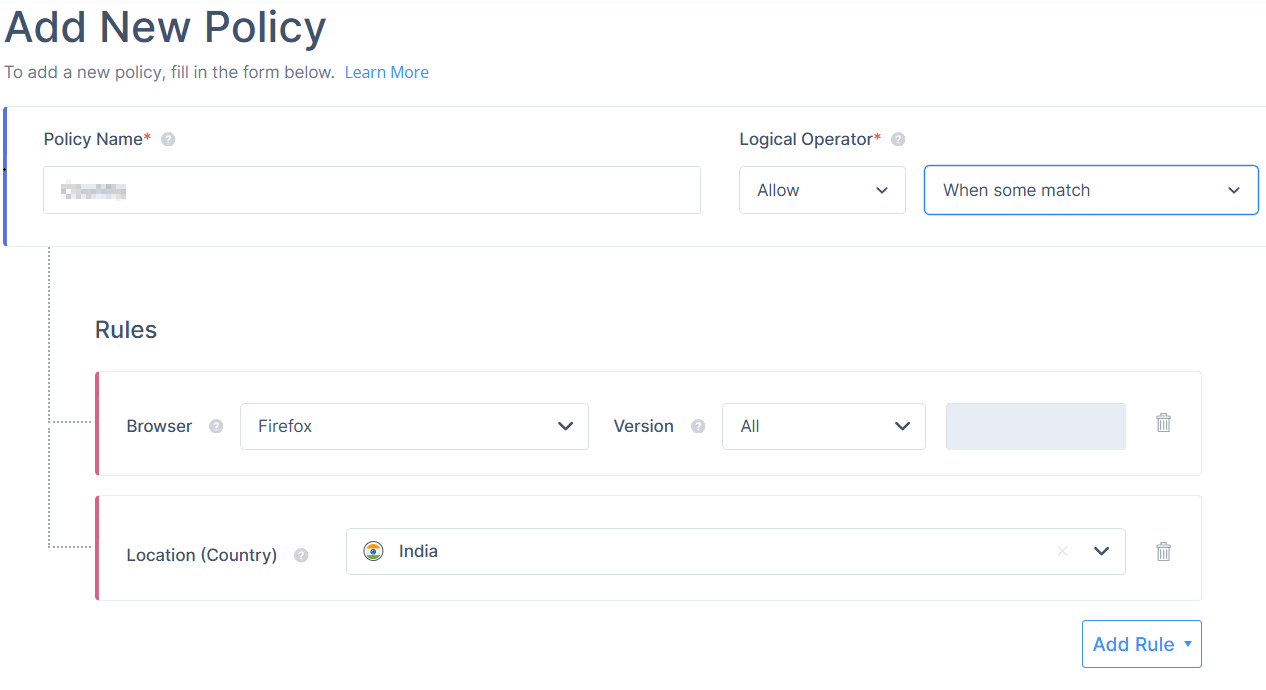
- Browser: Firefox
- Location (Country): India
In this scenario, access is allowed if either the user is using the Firefox browser or is located in India.
- Example 1: When all match
- From the policy action list, select either of these:
- Select the condition to apply the policy.
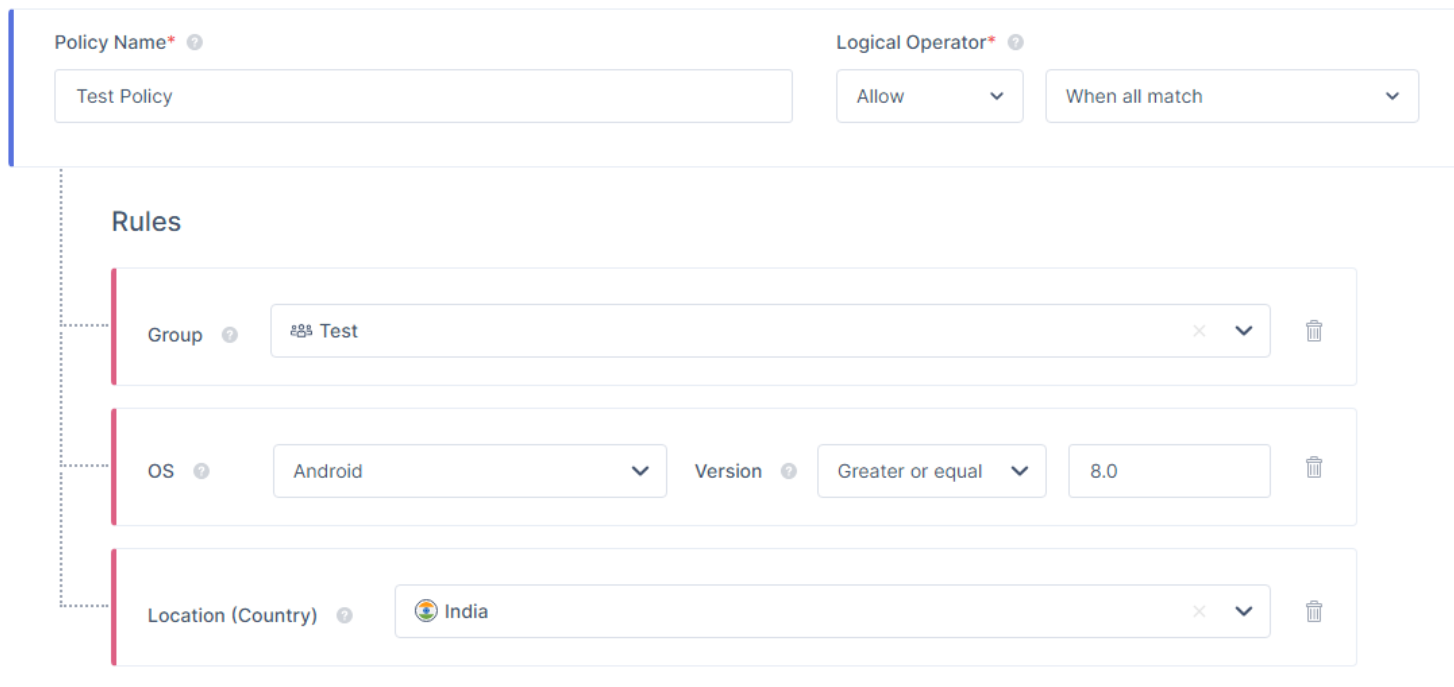
- To add the rules for the policy, click Add Rule and specify one or more of these options:
- Group
- Date and Time
- Location (IP)
- Location (Country)
- Browser
- OS and Version
- To attach an existing policy with the new policy, click Add Policy and select a policy.
- Click Save.
The new policy is listed in your Policy page.
Assigning a Policy to an Application
- Access the Harmony SASE Administrator Portal and click Private Access > Applications.
- Click
 for the application and click Edit.
for the application and click Edit.
- In the Policy section, from the Policy Name list, select a policy.
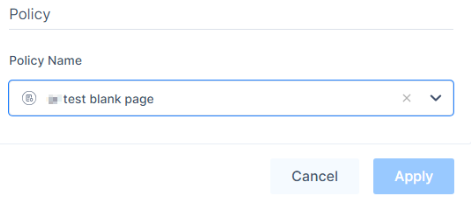
Click Apply.
Recommendations
- Always review your application access policies periodically to ensure they are up-to-date with organizational needs.
- Test new policies on a small group before rolling them out organization-wide.
Troubleshooting
If you encounter issues during or after the setup, try reviewing your settings to ensure everything matches the instructions. In particular, check the IP addresses and other details you entered during setup. If issues persist, please consult our dedicated support.
Support Contacts
If you have any difficulties or questions, don't hesitate to contact Perimeter 81's support team. We offer 24/7 chat support on our website at sase.checkpoint.com, or you can email us at sase-support@checkpoint.com. We're here to assist you and ensure your VPN tunnel setup is a success