Understanding Data Exporting to Microsoft Sentinel
This article describes how to set up and use Microsoft Sentinel (formerly Azure Sentinel). It is a scalable, cloud-native, security information event management (SIEM) and security orchestration automated response (SOAR) solution that integrates with the Harmony SASE platform. Azure Sentinel delivers intelligent security analytics and threat intelligence across the enterprise, providing a single solution for alert detection, threat visibility, proactive hunting, and threat response. You can configure your Harmony SASE data stream to Microsoft Sentinel to have full visibility of your Harmony SASE activity.
Setting up a Log Analytics workspace
If you are using an existing log analytics workspace, you may skip this part.
- Open the Azure portal and select Azure Sentinel.
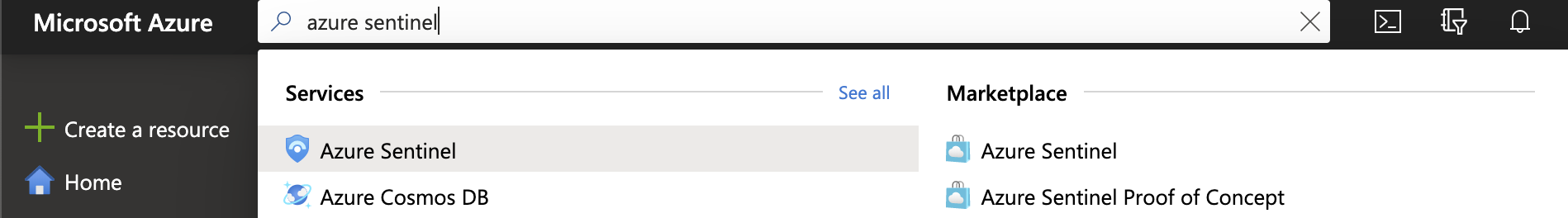
- Select +Add.
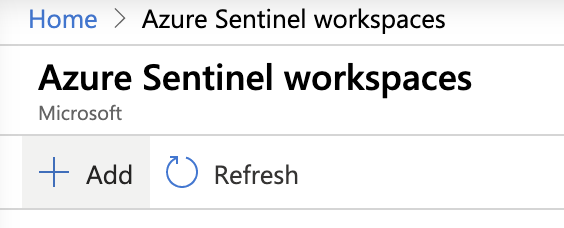
- Select Create a new workspace.
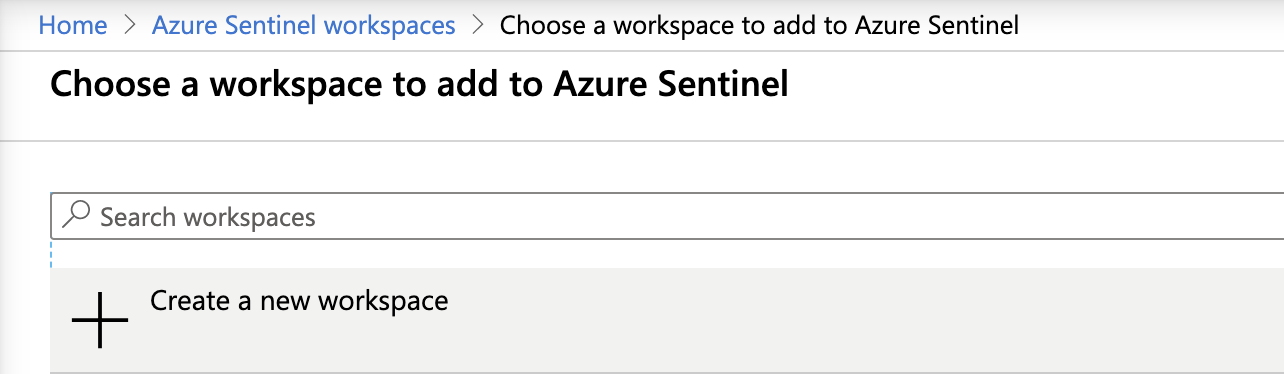
- Fill in the following information:
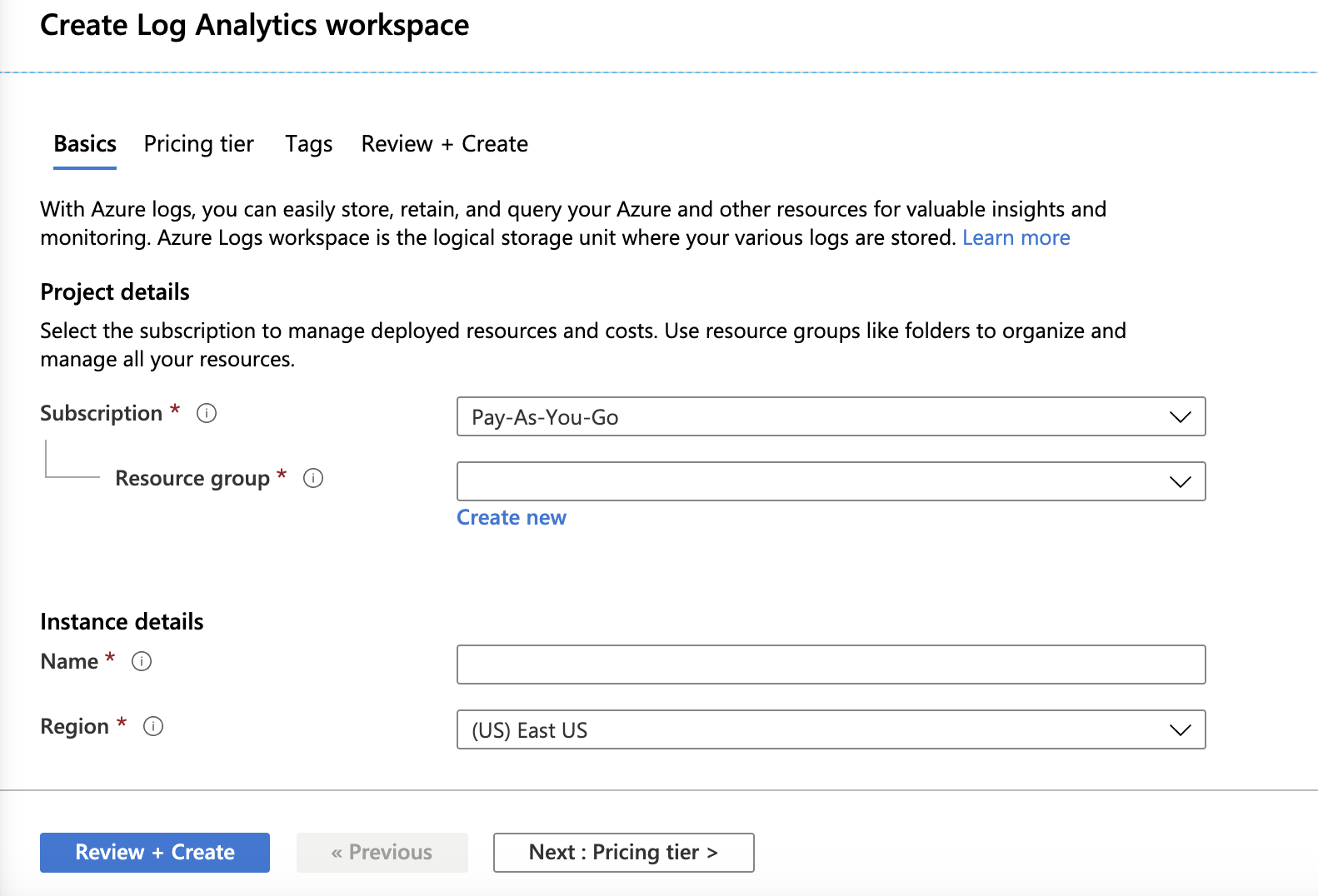
- Subscription: Choose a subscription according to your business's needs.
- Resource group: Associate the log analytics workspace with the appropriate business unit.
- Name: Choose the name of your own choice. The workspace name should include 4-63 letters, digits, or '-'. The '-' shouldn't be the first or the last symbol.
- Region: The physical location of the server generating the event collector. Choose according to pricing and business needs.
- (Optional) Review the pricing tiers and set appropriate tags for the workspace.
- Select Review + Create.
Linking the Logs Analytics workspace to Microsoft Sentinel
- Open the Azure portal and select Azure Sentinel.
- Select +Add.
- Select the Logs Analytics Workspace that you've just created or an existing one you'd like to utilize.
Finding your Log Analytics workspace ID and primary key
- Open Log Analytics Workspace.
- Select the workspace you've just connected to Microsoft Sentinel.
- Select Advanced settings.
- Select Connected Sources, then Linux Servers. Copy the Workspace ID as well as the Primary key.
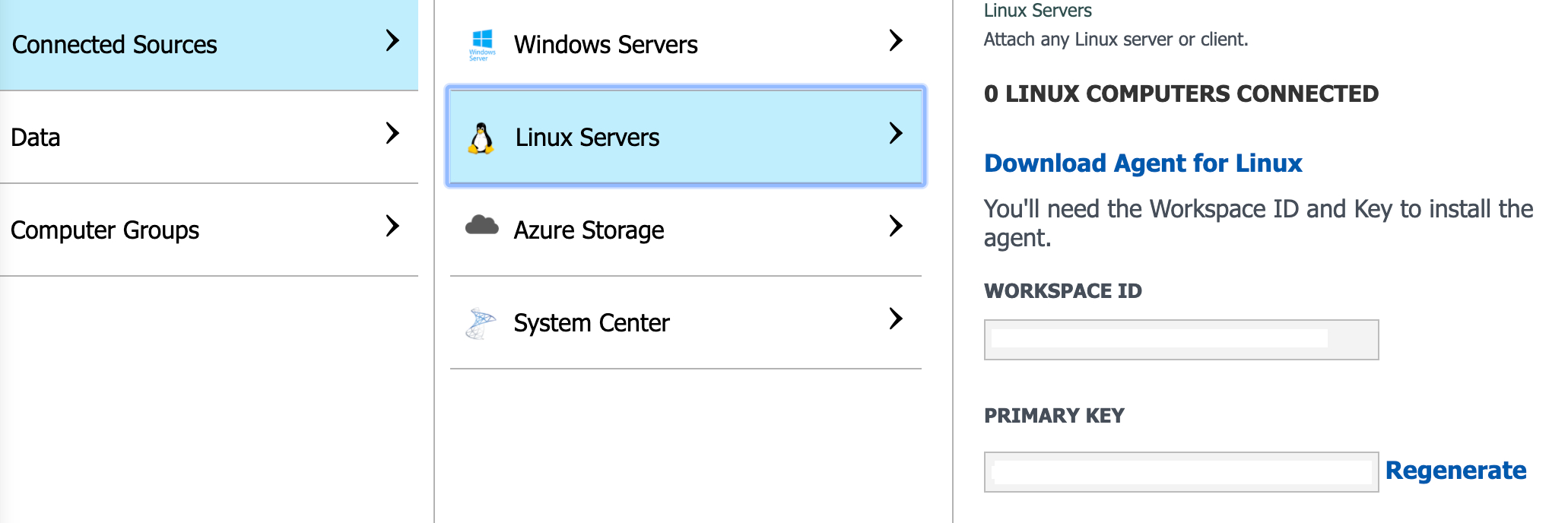
Configuring the integration at the Management Platform
- Log in to your Management Platform, navigate to Settings/Integrations, and select Add at the Microsoft Sentinel row.
- Fill in the values copied in the previous steps (the primary key will use as your workspace key).
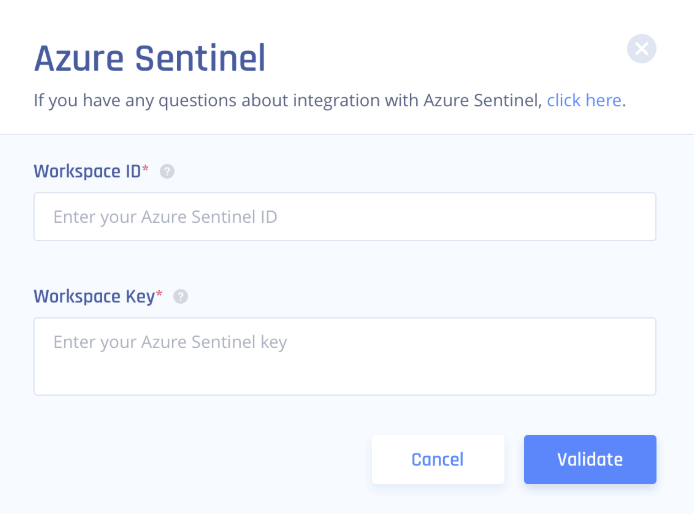
- Select Validate.
Recommendations
- When setting up the integration with Microsoft Sentinel, ensure that you have the correct Log Analytics Workspace ID and Primary Key.
- If you encounter error codes such as "SENTINEL_INACTIVE_CUSTOMER" or "SENTINEL_INVALID_AUTHORIZATION", review the provided workspace details and ensure they are accurate.
Troubleshooting
| Status Message | Action Required |
| Success | None. |
| SENTINEL_INACTIVE_CUSTOMER | The workspace has been deactivated. |
| SENTINEL_INVALID_CUSTOMER_ID | Please make sure you entered the correct customer ID. |
| SENTINEL_INVALID_AUTHORIZATION | The service failed to authenticate the request. Verify that the workspace ID and connection key are valid. |
Support Contacts
If you have any difficulties or questions, don't hesitate to contact Harmony SASE's support team. We offer 24/7 chat support on our website at sase.checkpoint.com, or you can email us at sase-support@checkpoint.com. We're here to assist you and ensure your VPN tunnel setup is a success.